EW_Skuzzy:1 VM Walkthrough
for the EW_Skuzzy:1 VM hosted on Vulnhub from vortexau.
I would have had a hard time with a lot of this VM if it weren’t for some very well-written resources found online. I didn’t however find the third flag because decryption wasn’t something that excited me that much and I was feeling lazy, I’ll revisit it when there are less VMs waiting I think.
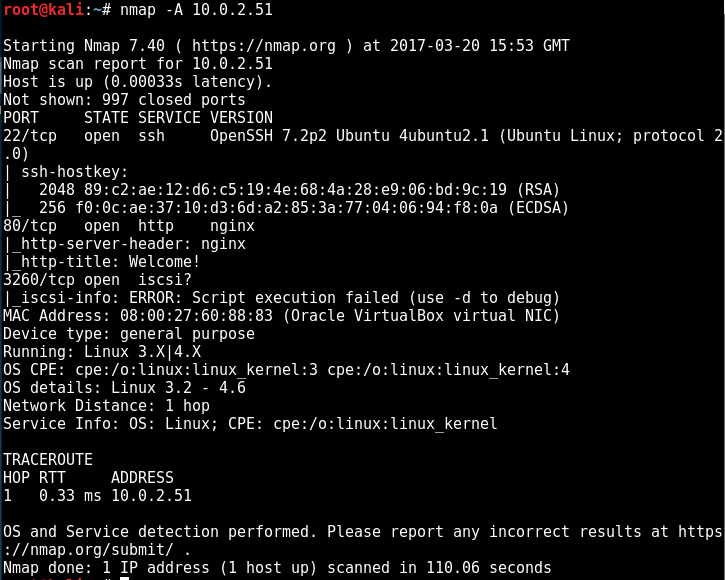
I started with the -A option on nmap this time round:
Port 80 is pretty standard but 3260 was new to me. Nikto doesn’t find anything on 80 so we’ll visit it through the browser:
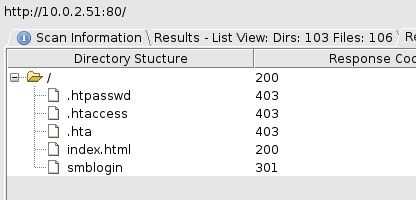
The main page gives us some advice and asks us to fire up dirbuster, so I do that:
We find an smblogin page, but I didn’t end up doing anything with that.
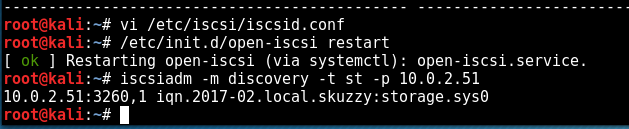
Now let’s look at that iscsi port; this resource helped me through this stage:
https://www.pentestpartners.com/blog/an-interesting-route-to-domain-admin-iscsi/
So following this guide, we first run the discovery:
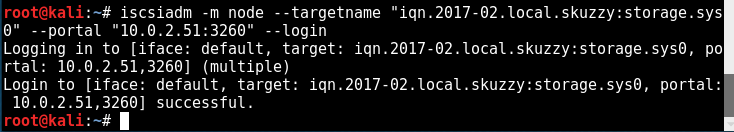
and then attempt to login, which is successful:
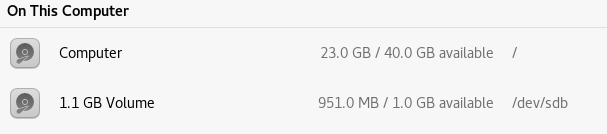
I initially got a bit lost at this point trying to mount the new drive, but the thing was in my file explorer anyway…
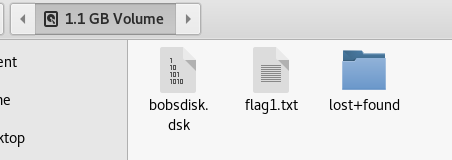
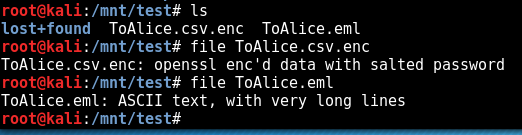
And inside that we find some files:
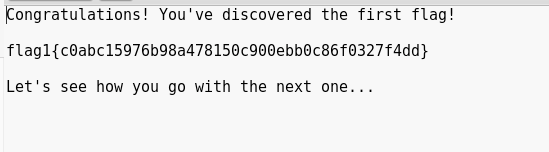
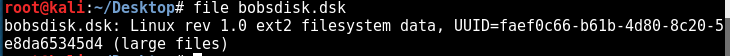
The first is flag 1 and the second is a disk image:
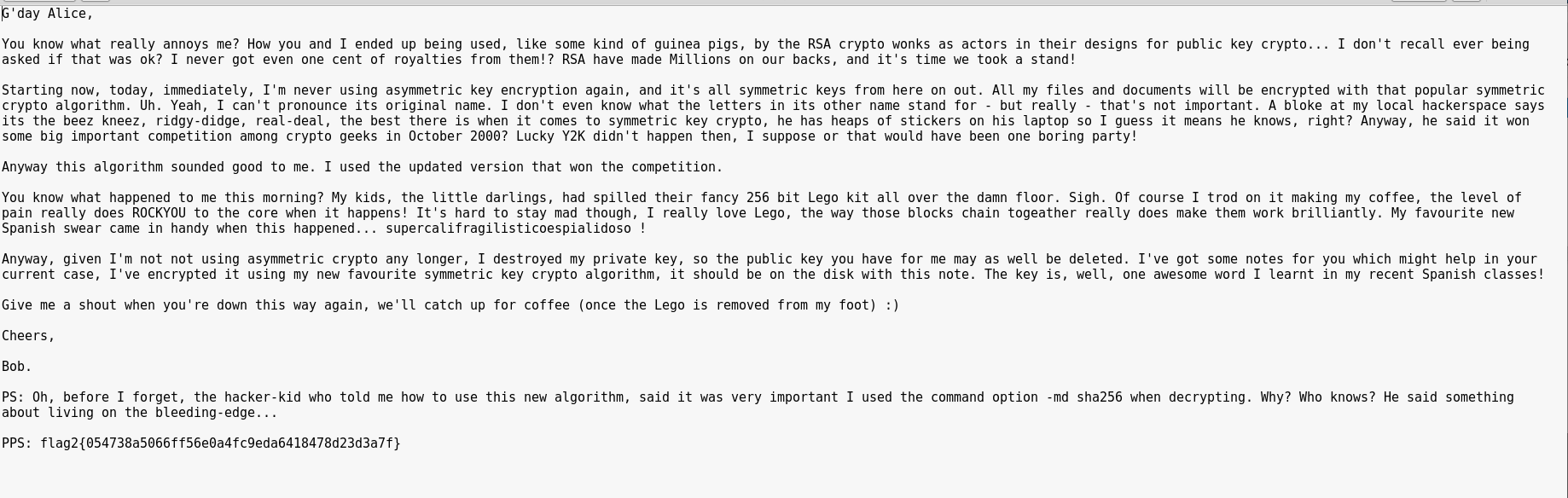
So when we mount the disk image we get an encrypted CSV and and email giving clues on how to decrypt the sha256 CSV using openssl :
and the email, which contains flag 2: