Kioptrix 3 VM Walkthrough
for the kioptrix3 VM hosted on Vulnhub from Kioptrix.
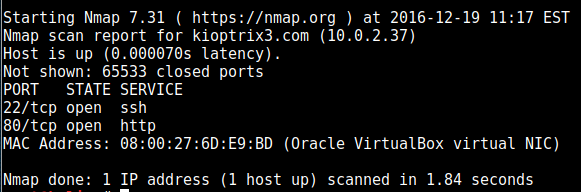
First off, nmap found the following ports open:
Some analysis using Nikto on port 80 also shows the location of a phpmyadmin install, but we’ll remember it for later as we have no credentials yet.
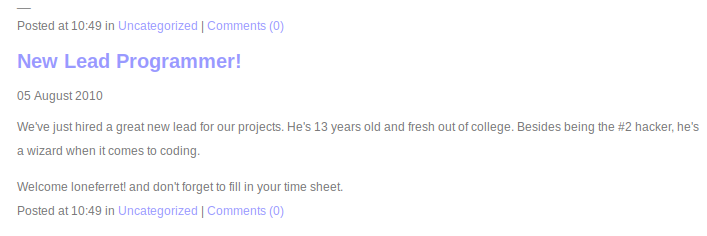
Browsing the website, we see a blog post which helps us enumerate a possible high-level user “loneferret”:
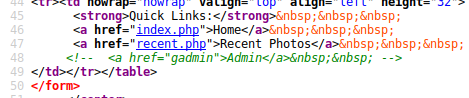
The gallery page also has a commented out link to an admin page:
Which leads to a “Gallarific” login screen:
Looking for exploits to the gallery software used, we find an SQL injection vulnerability at https://www.exploit-db.com/exploits/15891/
Although this doesn’t work fully in this instance, it does give us an SQL error message, which shows that the vulnerability exist in some form. The easiest way to find and exploit this is just to feed it into sqlmap and let that do the hunting, so after a few minutes we get a password hash in md5 which decrypts to fuckeyou
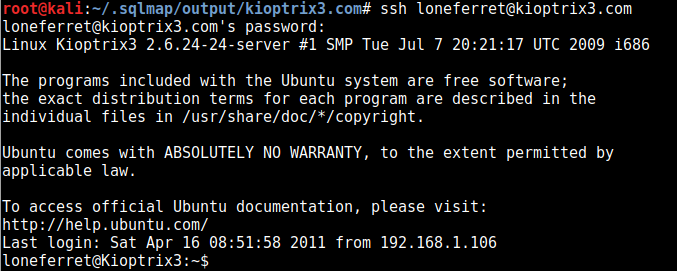
I tried this as an SSH password but it doesn’t accept it, but going back to that phpmyadmin page and it lets us in there.
Now looking through the database content in phpmyadmin we find another password hash located in the dev_accounts table, again in md5 which decrypts easily to starwars
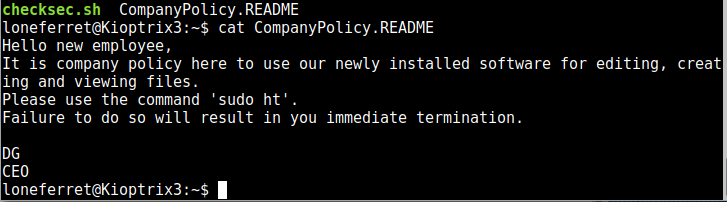
We can see a message for this user in their home folder:
“ht”, mentioned here, is an editor which on this system runs as root. I tried to run it but I kept getting error messages regarding xterm-256-colour, but this was easily fixed after a quick search of the message on Google:
export TERM=xterm-color
Which opens the editor for us, which I then use to edit the sudoers file to give the loneferret user sudo permissions:
so we use our sudo permission to open a shell with sudo /bin/bash which gives us a root prompt, and now to prove we have root access we can navigate to the root directory and view the flag: