Kioptrix 2 VM Walkthrough
for the kioptrix2 VM hosted on Vulnhub from Kioptrix.
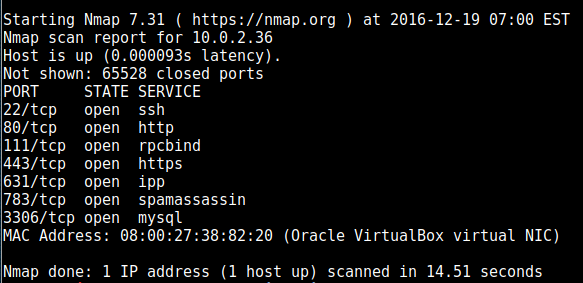
First off, nmap found the following ports open:
On port 80 we get a prompt for a username and password. Because it looks a bit amateurish we can try some sql injections. The source tells us the username is Administator [sic], but rockyou would have been overkill, as using this as the password got me entry:
‘or’1’=’1
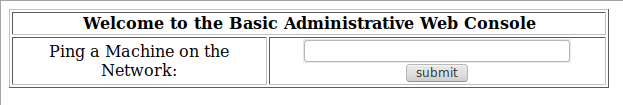
so now we have a box allowing us to enter an IP to ping:
Now we know that the amateurish front-end is also a sign of the state of the back-end which doesn’t sanitize input, so the fact that it’s allowing us to provide parameters for a system command is very exciting.
to try it out, I entered this as the IP first:
10.0.2.32 & curl –help
which showed me the curl help info! So the next step is to inject a small command shell. I grabbed one from pentestmonkey’s webshell cheatsheet
I chose the Perl one, after checking that perl works by sending perl -v to the ping command as I did with curl, above.
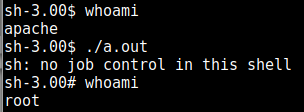
When I access that file from the browser and send a command to run it works (albeit limited) so I start the apache2 service on my kali VM and place my php reverse webshell there (after configuring it to point to the kali ip and port). which successfully gets me a limited shell.
After using uname -a to enumerate the linux kernel, I find an exploit here https://www.exploit-db.com/exploits/9542/ which grants me root access: